Link Layer: Introduction - PowerPoint PPT Presentation
1 / 76
Title:
Link Layer: Introduction
Description:
Internet radio talk show. Live sporting event. Streaming. playback buffer ... for every group of n chunks create a redundant chunk by exclusive OR-ing the n ... – PowerPoint PPT presentation
Number of Views:77
Avg rating:3.0/5.0
Title: Link Layer: Introduction
1
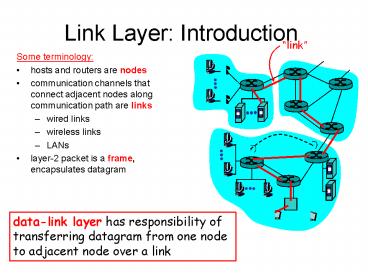
Link Layer Introduction
- Some terminology
- hosts and routers are nodes
- communication channels that connect adjacent
nodes along communication path are links - wired links
- wireless links
- LANs
- layer-2 packet is a frame, encapsulates datagram
data-link layer has responsibility of
transferring datagram from one node to adjacent
node over a link
2
Error Detection
- EDC Error Detection and Correction bits
(redundancy) - D Data protected by error checking, may
include header fields - Error detection not 100 reliable!
- protocol may miss some errors, but rarely
- larger EDC field yields better detection and
correction
3
Parity Checking
Two Dimensional Bit Parity Detect and correct
single bit errors
Single Bit Parity Detect single bit errors
0
0
4
MAC Protocols a taxonomy
- Three broad classes
- Channel Partitioning
- divide channel into smaller pieces (time slots,
frequency, code) - allocate piece to node for exclusive use
- Random Access
- channel not divided, allow collisions
- recover from collisions
- Taking turns
- Nodes take turns, but nodes with more to send can
take longer turns
5
Channel Partitioning MAC protocols TDMA
- TDMA time division multiple access
- access to channel in "rounds"
- each station gets fixed length slot (length pkt
trans time) in each round - unused slots go idle
- example 6-station LAN, 1,3,4 have pkt, slots
2,5,6 idle - TDM (Time Division Multiplexing) channel divided
into N time slots, one per user inefficient with
low duty cycle users and at light load. - FDM (Frequency Division Multiplexing) frequency
subdivided.
6
Channel Partitioning MAC protocols FDMA
- FDMA frequency division multiple access
- channel spectrum divided into frequency bands
- each station assigned fixed frequency band
- unused transmission time in frequency bands go
idle - example 6-station LAN, 1,3,4 have pkt, frequency
bands 2,5,6 idle - TDM (Time Division Multiplexing) channel divided
into N time slots, one per user inefficient with
low duty cycle users and at light load. - FDM (Frequency Division Multiplexing) frequency
subdivided.
time
frequency bands
7
Taking Turns MAC protocols
- channel partitioning MAC protocols
- share channel efficiently and fairly at high load
- inefficient at low load delay in channel access,
1/N bandwidth allocated even if only 1 active
node! - Random access MAC protocols
- efficient at low load single node can fully
utilize channel - high load collision overhead
- taking turns protocols
- look for best of both worlds!
8
Taking Turns MAC protocols
- Token passing
- control token passed from one node to next
sequentially. - token message
- concerns
- token overhead
- latency
- single point of failure (token)
- Polling
- master node invites slave nodes to transmit in
turn - concerns
- polling overhead
- latency
- single point of failure (master)
9
MAC Addresses and ARP
- 32-bit IP address
- network-layer address
- used to get datagram to destination IP subnet
- MAC (or LAN or physical or Ethernet) address
- used to get frame from one interface to another
physically-connected interface (same network) - 48 bit MAC address (for most LANs) burned in the
adapter ROM
10
LAN Address (more)
- MAC address allocation administered by IEEE
- manufacturer buys portion of MAC address space
(to assure uniqueness) - Analogy
- (a) MAC address like Social Security
Number - (b) IP address like postal address
- MAC flat address ? portability
- can move LAN card from one LAN to another
- IP hierarchical address NOT portable
- depends on IP subnet to which node is attached
11
DHCP Dynamic Host Configuration Protocol
- Goal allow host to dynamically obtain its IP
address from network server when it joins network - Can renew its lease on address in use
- Allows reuse of addresses (only hold address
while connected an on - Support for mobile users who want to join network
(more shortly) - DHCP overview
- host broadcasts DHCP discover msg
- DHCP server responds with DHCP offer msg
- host requests IP address DHCP request msg
- DHCP server sends address DHCP ack msg
12
Ethernet Frame Structure
- Sending adapter encapsulates IP datagram (or
other network layer protocol packet) in Ethernet
frame - Preamble
- 7 bytes with pattern 10101010 followed by one
byte with pattern 10101011 - used to synchronize receiver, sender clock rates
13
Ethernet Frame Structure (more)
- Addresses 6 bytes
- if adapter receives frame with matching
destination address, or with broadcast address
(eg ARP packet), it passes data in frame to
net-layer protocol - otherwise, adapter discards frame
- Type indicates the higher layer protocol (mostly
IP but others may be supported such as Novell IPX
and AppleTalk) - CRC checked at receiver, if error is detected,
the frame is simply dropped
14
Hubs
- Hubs are essentially physical-layer repeaters
- bits coming from one link go out all other links
- at the same rate
- no frame buffering
- no CSMA/CD at hub adapters detect collisions
- provides net management functionality
15
Interconnecting with hubs
- Backbone hub interconnects LAN segments
- Extends max distance between nodes
- But individual segment collision domains become
one large collision domain - Cant interconnect 10BaseT 100BaseT
hub
hub
hub
hub
16
Switch
- Link layer device
- stores and forwards Ethernet frames
- examines frame header and selectively forwards
frame based on MAC dest address - when frame is to be forwarded on segment, uses
CSMA/CD to access segment - transparent
- hosts are unaware of presence of switches
- plug-and-play, self-learning
- switches do not need to be configured
17
Forwarding
1
3
2
- How do determine onto which LAN segment to
forward frame? - Looks like a routing problem...
18
Switches dedicated access
- Switch with many interfaces
- Hosts have direct connection to switch
- No collisions full duplex
- Switching A-to-A and B-to-B simultaneously, no
collisions
A
C
B
switch
C
B
A
19
Point to Point Data Link Control
- one sender, one receiver, one link easier than
broadcast link - no Media Access Control
- no need for explicit MAC addressing
- e.g., dialup link, ISDN line
- popular point-to-point DLC protocols
- PPP (point-to-point protocol)
- HDLC High level data link control (Data link
used to be considered high layer in protocol
stack!
20
PPP non-requirements
- no error correction/recovery
- no flow control
- out of order delivery OK
- no need to support multipoint links (e.g.,
polling)
Error recovery, flow control, data re-ordering
all relegated to higher layers!
21
PPP Data Frame
- Flag delimiter (framing)
- Address does nothing (only one option)
- Control does nothing in the future possible
multiple control fields - Protocol upper layer protocol to which frame
delivered (eg, PPP-LCP, IP, IPCP, etc)
22
PPP Data Control Protocol
- Before exchanging network-layer data, data link
peers must - configure PPP link (max. frame length,
authentication) - learn/configure network
- layer information
- for IP carry IP Control Protocol (IPCP) msgs
(protocol field 8021) to configure/learn IP
address
23
Chapter 6 Wireless and Mobile Networks
- Background
- wireless (mobile) phone subscribers now exceeds
wired phone subscribers! - computer nets laptops, palmtops, PDAs,
Internet-enabled phone promise anytime untethered
Internet access - two important (but different) challenges
- communication over wireless link
- handling mobile user who changes point of
attachment to network
24
Characteristics of selected wireless link
standards
54 Mbps
802.11a,g
5-11 Mbps
.11 p-to-p link
802.11b
1 Mbps
802.15
3G
384 Kbps
UMTS/WCDMA, CDMA2000
2G
56 Kbps
IS-95 CDMA, GSM
25
Wireless Link Characteristics
- Differences from wired link .
- decreased signal strength radio signal
attenuates as it propagates through matter (path
loss) - interference from other sources standardized
wireless network frequencies (e.g., 2.4 GHz)
shared by other devices (e.g., phone) devices
(motors) interfere as well - multipath propagation radio signal reflects off
objects ground, arriving ad destination at
slightly different times - . make communication across (even a point to
point) wireless link much more difficult
26
Code Division Multiple Access (CDMA)
- used in several wireless broadcast channels
(cellular, satellite, etc) standards - unique code assigned to each user i.e., code
set partitioning - all users share same frequency, but each user has
own chipping sequence (i.e., code) to encode
data - encoded signal (original data) X (chipping
sequence) - decoding inner-product of encoded signal and
chipping sequence - allows multiple users to coexist and transmit
simultaneously with minimal interference (if
codes are orthogonal)
27
IEEE 802.11 Wireless LAN
- 802.11b
- 2.4-5 GHz unlicensed radio spectrum
- up to 11 Mbps
- direct sequence spread spectrum (DSSS) in
physical layer - all hosts use same chipping code
- widely deployed, using base stations
- 802.11a
- 5-6 GHz range
- up to 54 Mbps
- 802.11g
- 2.4-5 GHz range
- up to 54 Mbps
- All use CSMA/CA for multiple access
- All have base-station and ad-hoc network versions
28
802.11 frame addressing
Address 4 used only in ad hoc mode
Address 1 MAC address of wireless host or AP to
receive this frame
Address 3 MAC address of router interface to
which AP is attached
Address 2 MAC address of wireless host or AP
transmitting this frame
29
802.11 frame more
frame seq (for reliable ARQ)
duration of reserved transmission time (RTS/CTS)
frame type (RTS, CTS, ACK, data)
30
Mobility via Indirect Routing
visited network
home network
wide area network
31
Indirect Routing comments
- Mobile uses two addresses
- permanent address used by correspondent (hence
mobile location is transparent to correspondent) - care-of-address used by home agent to forward
datagrams to mobile - foreign agent functions may be done by mobile
itself - triangle routing correspondent-home-network-mobil
e - inefficient when
- correspondent, mobile
- are in same network
32
Mobility via Direct Routing
correspondent forwards to foreign agent
visited network
home network
wide area network
correspondent requests, receives foreign address
of mobile
33
Multimedia, Quality of Service What is it?
Multimedia applications network audio and
video (continuous media)
34
MM Networking Applications
- Fundamental characteristics
- Typically delay sensitive
- end-to-end delay
- delay jitter
- But loss tolerant infrequent losses cause minor
glitches - Antithesis of data, which are loss intolerant but
delay tolerant.
Classes of MM applications 1) Streaming stored
audio and video 2) Streaming live audio and
video 3) Real-time interactive audio and video
Jitter is the variability of packet delays
within the same packet stream
35
Streaming Stored Multimedia
- Streaming
- media stored at source
- transmitted to client
- streaming client playout begins before all data
has arrived
- timing constraint for still-to-be transmitted
data in time for playout
36
Streaming Live Multimedia
- Examples
- Internet radio talk show
- Live sporting event
- Streaming
- playback buffer
- playback can lag tens of seconds after
transmission - still have timing constraint
- Interactivity
- fast forward impossible
- rewind, pause possible!
37
How should the Internet evolve to better support
multimedia?
- Integrated services philosophy
- Fundamental changes in Internet so that apps can
reserve end-to-end bandwidth - Requires new, complex software in hosts routers
- Laissez-faire
- no major changes
- more bandwidth when needed
- content distribution, application-layer multicast
- application layer
- Differentiated services philosophy
- Fewer changes to Internet infrastructure, yet
provide 1st and 2nd class service.
Whats your opinion?
38
A few words about audio compression
- Analog signal sampled at constant rate
- telephone 8,000 samples/sec
- CD music 44,100 samples/sec
- Each sample quantized, i.e., rounded
- e.g., 28256 possible quantized values
- Each quantized value represented by bits
- 8 bits for 256 values
- Example 8,000 samples/sec, 256 quantized values
--gt 64,000 bps - Receiver converts it back to analog signal
- some quality reduction
- Example rates
- CD 1.411 Mbps
- MP3 96, 128, 160 kbps
- Internet telephony 5.3 - 13 kbps
39
A few words about video compression
- Video is sequence of images displayed at constant
rate - e.g. 24 images/sec
- Digital image is array of pixels
- Each pixel represented by bits
- Redundancy
- spatial
- temporal
- Examples
- MPEG 1 (CD-ROM) 1.5 Mbps
- MPEG2 (DVD) 3-6 Mbps
- MPEG4 (often used in Internet, lt 1 Mbps)
- Research
- Layered (scalable) video
- adapt layers to available bandwidth
40
Internet multimedia simplest approach
- audio or video stored in file
- files transferred as HTTP object
- received in entirety at client
- then passed to player
- audio, video not streamed
- no, pipelining, long delays until playout!
41
Internet multimedia streaming approach
- browser GETs metafile
- browser launches player, passing metafile
- player contacts server
- server streams audio/video to player
42
Streaming from a streaming server
- This architecture allows for non-HTTP protocol
between server and media player - Can also use UDP instead of TCP.
43
User Control of Streaming Media RTSP
- What it doesnt do
- does not define how audio/video is encapsulated
for streaming over network - does not restrict how streamed media is
transported it can be transported over UDP or
TCP - does not specify how the media player buffers
audio/video
- HTTP
- Does not target multimedia content
- No commands for fast forward, etc.
- RTSP RFC 2326
- Client-server application layer protocol.
- For user to control display rewind, fast
forward, pause, resume, repositioning, etc
44
Recovery from packet loss (1)
- forward error correction (FEC) simple scheme
- for every group of n chunks create a redundant
chunk by exclusive OR-ing the n original chunks - send out n1 chunks, increasing the bandwidth by
factor 1/n. - can reconstruct the original n chunks if there is
at most one lost chunk from the n1 chunks
- Playout delay needs to be fixed to the time to
receive all n1 packets - Tradeoff
- increase n, less bandwidth waste
- increase n, longer playout delay
- increase n, higher probability that 2 or more
chunks will be lost
45
Recovery from packet loss (2)
- 2nd FEC scheme
- piggyback lower quality stream
- send lower resolutionaudio stream as
theredundant information - for example, nominal stream PCM at 64 kbpsand
redundant streamGSM at 13 kbps.
- Whenever there is non-consecutive loss,
thereceiver can conceal the loss. - Can also append (n-1)st and (n-2)nd low-bit
ratechunk
46
Recovery from packet loss (3)
- Interleaving
- chunks are brokenup into smaller units
- for example, 4 5 msec units per chunk
- Packet contains small units from different chunks
- if packet is lost, still have most of every chunk
- has no redundancy overhead
- but adds to playout delay
47
What is network security?
- Confidentiality only sender, intended receiver
should understand message contents - sender encrypts message
- receiver decrypts message
- Authentication sender, receiver want to confirm
identity of each other - Message Integrity sender, receiver want to
ensure message not altered (in transit, or
afterwards) without detection - Access and Availability services must be
accessible and available to users
48
Friends and enemies Alice, Bob, Trudy
- well-known in network security world
- Bob, Alice (lovers!) want to communicate
securely - Trudy (intruder) may intercept, delete, add
messages
Alice
Bob
data, control messages
channel
secure sender
secure receiver
data
data
Trudy
49
There are bad guys (and girls) out there!
- Q What can a bad guy do?
- A a lot!
- eavesdrop intercept messages
- actively insert messages into connection
- impersonation can fake (spoof) source address in
packet (or any field in packet) - hijacking take over ongoing connection by
removing sender or receiver, inserting himself in
place - denial of service prevent service from being
used by others (e.g., by overloading resources)
50
The language of cryptography
Alices encryption key
Bobs decryption key
encryption algorithm
decryption algorithm
ciphertext
plaintext
plaintext
symmetric key crypto sender, receiver keys
identical public-key crypto encryption key
public, decryption key secret (private)
51
Symmetric key cryptography
- substitution cipher substituting one thing for
another - monoalphabetic cipher substitute one letter for
another
plaintext abcdefghijklmnopqrstuvwxyz
ciphertext mnbvcxzasdfghjklpoiuytrewq
E.g.
Plaintext bob. i love you. alice
ciphertext nkn. s gktc wky. mgsbc
- Q How hard to break this simple cipher?
- brute force (how hard?)
- other?
52
Symmetric key cryptography
encryption algorithm
decryption algorithm
ciphertext
plaintext
plaintext message, m
K (m)
A-B
- symmetric key crypto Bob and Alice share know
same (symmetric) key K - e.g., key is knowing substitution pattern in mono
alphabetic substitution cipher - Q how do Bob and Alice agree on key value?
A-B
53
Public Key Cryptography
- symmetric key crypto
- requires sender, receiver know shared secret key
- Q how to agree on key in first place
(particularly if never met)?
- public key cryptography
- radically different approach Diffie-Hellman76,
RSA78 - sender, receiver do not share secret key
- public encryption key known to all
- private decryption key known only to receiver
54
Public key cryptography
Bobs public key
K
B
-
Bobs private key
K
B
encryption algorithm
decryption algorithm
plaintext message
plaintext message, m
ciphertext
55
Public key encryption algorithms
Requirements
.
.
-
need K ( ) and K ( ) such that
B
B
given public key K , it should be impossible to
compute private key K
B
-
B
RSA Rivest, Shamir, Adelson algorithm
56
RSA Choosing keys
1. Choose two large prime numbers p, q.
(e.g., 1024 bits each)
2. Compute n pq, z (p-1)(q-1)
3. Choose e (with eltn) that has no common
factors with z. (e, z are relatively prime).
4. Choose d such that ed-1 is exactly divisible
by z. (in other words ed mod z 1 ).
5. Public key is (n,e). Private key is (n,d).
57
RSA another important property
The following property will be very useful later
use public key first, followed by private key
use private key first, followed by public key
Result is the same!
58
Authentication
Goal Bob wants Alice to prove her identity to
him
Protocol ap1.0 Alice says I am Alice
I am Alice
Failure scenario??
59
Authentication
Goal Bob wants Alice to prove her identity to
him
Protocol ap1.0 Alice says I am Alice
in a network, Bob can not see Alice, so Trudy
simply declares herself to be Alice
I am Alice
60
Authentication another try
Protocol ap2.0 Alice says I am Alice in an IP
packet containing her source IP address
Failure scenario??
61
Authentication another try
Protocol ap2.0 Alice says I am Alice in an IP
packet containing her source IP address
Trudy can create a packet spoofing Alices
address
62
Authentication another try
Protocol ap3.0 Alice says I am Alice and sends
her secret password to prove it.
Failure scenario??
63
Authentication another try
Protocol ap3.0 Alice says I am Alice and sends
her secret password to prove it.
Alices password
Alices IP addr
Im Alice
playback attack Trudy records Alices packet and
later plays it back to Bob
64
Authentication yet another try
Protocol ap3.1 Alice says I am Alice and sends
her encrypted secret password to prove it.
Failure scenario??
65
Authentication another try
Protocol ap3.1 Alice says I am Alice and sends
her encrypted secret password to prove it.
encrypted password
Alices IP addr
record and playback still works!
Im Alice
66
Authentication yet another try
Goal avoid playback attack
Nonce number (R) used only once in-a-lifetime
ap4.0 to prove Alice live, Bob sends Alice
nonce, R. Alice must return R, encrypted with
shared secret key
I am Alice
R
Alice is live, and only Alice knows key to
encrypt nonce, so it must be Alice!
Failures, drawbacks?
67
ap5.0 security hole
- Man (woman) in the middle attack Trudy poses as
Alice (to Bob) and as Bob (to Alice)
I am Alice
I am Alice
R
R
Send me your public key
Send me your public key
Trudy gets
sends m to Alice encrypted with Alices public key
68
Digital Signatures
- Simple digital signature for message m
- Bob signs m by encrypting with his private key
KB, creating signed message, KB(m)
-
-
Bobs private key
Bobs message, m
(m)
Dear Alice Oh, how I have missed you. I think of
you all the time! (blah blah blah) Bob
Bobs message, m, signed (encrypted) with his
private key
Public key encryption algorithm
69
Trusted Intermediaries
- Symmetric key problem
- How do two entities establish shared secret key
over network? - Solution
- trusted key distribution center (KDC) acting as
intermediary between entities
- Public key problem
- When Alice obtains Bobs public key (from web
site, e-mail, diskette), how does she know it is
Bobs public key, not Trudys? - Solution
- trusted certification authority (CA)
70
Firewalls Why
- prevent denial of service attacks
- SYN flooding attacker establishes many bogus TCP
connections, no resources left for real
connections. - prevent illegal modification/access of internal
data. - e.g., attacker replaces CIAs homepage with
something else - allow only authorized access to inside network
(set of authenticated users/hosts) - two types of firewalls
- application-level
- packet-filtering
71
Limitations of firewalls and gateways
- IP spoofing router cant know if data really
comes from claimed source - if multiple apps. need special treatment, each
has own app. gateway. - client software must know how to contact gateway.
- e.g., must set IP address of proxy in Web browser
- filters often use all or nothing policy for UDP.
- tradeoff degree of communication with outside
world, level of security - many highly protected sites still suffer from
attacks.
72
What is network management?
- autonomous systems (aka network) 100s or 1000s
of interacting hardware/software components - other complex systems requiring monitoring,
control - jet airplane
- nuclear power plant
- others?
"Network management includes the deployment,
integration and coordination of the hardware,
software, and human elements to monitor, test,
poll, configure, analyze, evaluate, and control
the network and element resources to meet the
real-time, operational performance, and Quality
of Service requirements at a reasonable cost."
73
Network Management standards
- OSI CMIP
- Common Management Information Protocol
- designed 1980s the unifying net management
standard - too slowly standardized
- SNMP Simple Network Management Protocol
- Internet roots (SGMP)
- started simple
- deployed, adopted rapidly
- growth size, complexity
- currently SNMP V3
- de facto network management standard
74
SNMP overview 4 key parts
- Management information base (MIB)
- distributed information store of network
management data - Structure of Management Information (SMI)
- data definition language for MIB objects
- SNMP protocol
- convey managerlt-gtmanaged object info, commands
- security, administration capabilities
- major addition in SNMPv3
75
Presentation problem potential solutions
- 1. Sender learns receivers format. Sender
translates into receivers format. Sender sends. - real-world analogy?
- pros and cons?
- 2. Sender sends. Receiver learns senders format.
Receiver translate into receiver-local format - real-world-analogy
- pros and cons?
- 3. Sender translates host-independent format.
Sends. Receiver translates to receiver-local
format. - real-world analogy?
- pros and cons?
76
Solving the presentation problem
- 1. Translate local-host format to
host-independent format - 2. Transmit data in host-independent format
- 3. Translate host-independent format to
remote-host format
aging 60s hippie
2004 teenager
grandma