Introduction to Network Management - PowerPoint PPT Presentation
1 / 97
Title:
Introduction to Network Management
Description:
the process of ensuring that the users of a network receive the IT services with ... deprecated, obsolete. Description: textual definition. of the object type. page 31 ... – PowerPoint PPT presentation
Number of Views:758
Avg rating:3.0/5.0
Title: Introduction to Network Management
1
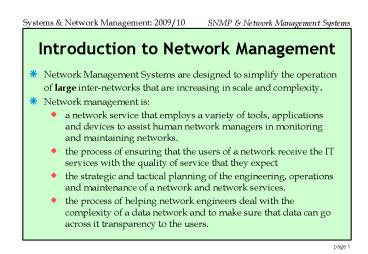
Introduction to Network Management
- Network Management Systems are designed to
simplify the operation of large inter-networks
that are increasing in scale and complexity. - Network management is
- a network service that employs a variety of
tools, applications and devices to assist human
network managers in monitoring and maintaining
networks. - the process of ensuring that the users of a
network receive the IT services with the quality
of service that they expect - the strategic and tactical planning of the
engineering, operations and maintenance of a
network and network services. - the process of helping network engineers deal
with the complexity of a data network and to make
sure that data can go across it transparency to
the users.
2
Functions of Network Management
- control corporate strategic assets from a central
position - aids in strategically planning for network growth
- provide remote system management
- operate independently of the system it monitors
- support multiple protocols
- operate as transparently as possible
- improve services - maintaining network stability,
tuning network performance - balance various needs - applications, systems and
technologies - troubleshooting problems that might arise
- reduce downtime with fast response time
- control costs
3
Challenges
- Network monitoring
- Network conditions is more visible and can alert
network administrators to problems quickly. - Automated processes
- Repetitive tasks can be performed reliably and
predictably - Integration across diverse network environments
(heterogeneous networks) - Management capabilities can be made available in
geographically dispersed networks using multiple
protocols or platforms. - Tracking functions
- Tracking past problems makes finding solutions
easier, while recording values for performance,
availability, and other areas can uncover trends
that might affect future growth.
4
Network Management Styles
- BAD
- User the server has been down for an hour, and
printing has stopped working, and the connection
to the Internet is down. - System manager lets have a look and see what we
can do. - BETTER
- User the server has just gone down, and printing
has stopped working, and the connection to the
Internet is down. - System manager we have been working on it, we
know that this is a problem with our main switch,
we are working to solve the problem. - BEST If there is a good Network Management
System - The user does not see any problem
- The system managers could see from trends in the
network traffic that there was a problem, e.g.,
number of bad packets - The problem was fixed before the users were aware
of it.
5
ISO Network Management Model
- The ISO Network Management Model (FCAPS) defines
5 areas of network management issues - Fault management
- Configuration management
- Accounting management
- Performance management
- Security management
6
FCAPS Model
- Fault management
- Fault management manages network problems in
order to keep the network running effectively - Configuration management
- Configuration management monitors network and
system configuration information - Accounting management
- Accounting management measures and regulates
network utilization - Performance management
- Performance management maintains inter-network
performance at acceptable levels - Security management
- Security management controls access to network
resources
7
Network Monitoring Information
- Network monitoring information can be classified
as Static, Dynamic and Statistical. - Static information, such as the number and
identification of interface ports on a router,
do not often change. - Dynamic information is about the state of network
devices and the events in the network. For
example, a change of state of a protocol, or, the
transmission of packets on a network. - Statistical information that can be derived from
dynamic information, such as the average number
of packets transmitted per unit time by a device.
8
Network Monitoring Information
- The nature of monitored information affects the
ways to collect and store them. - Static information is typically generated by the
device involved. For example, a router maintains
its own configuration information. - If a device is attached to a network, then some
of its activities (dynamic information) can be
observed by another device on the same network. - For example, the total number of packets
transmitted by a device on a network can be
recorded by the device itself, or by another
device (such as a remote monitor) that is
listening on the same network. - Some dynamic information, however, are only
generated by the device itself, such as the
current number of TCP connections.
9
Network Management Software
CiscoWorks for Windows
HP Open View for Windows
WINSOCK
10
Network Management Software
- Typical functions provided by network management
software - Configuration tools to remotely set IP address,
turn on or shut down an interface port, etc.. - Detect network devices and generate network
diagram - Alarm log displays special events. Alarm log
filter specifies types of events to be monitored. - A virtual view shows the status of interface
ports, and provides a easy way to further obtain
data or configure the device. - Collecting, analyzing and reporting
network/device status information - MRTG is an example of software that collects and
displays traffic information
11
Types of Management SystemsExample CiscoView
(Fault / Configuration Management)
- CiscoView
- A virtual view shows the status of interface
ports, and provides a easy way to further obtain
data or configure the device.
12
Types of Management SystemsExample CiscoWorks
(Configuration Management)
- Resource Manager
- Essentials and Campus Manager
- Knowledge of network configuration and topology
- Facilitates remote configuration of network
devices - Maintains an archive of configuration data that
allows generation of inventory reports
13
Types of Management SystemsExample MRTG
(Performance Management)
- Monitors traffic load on network links based on
SNMP statistics - Generates real-time HTMLtraffic reports
- Can be used to monitor any MIB variable using SNMP
14
NMS Components
15
Network Management Systems
- A typical model of network management system
consists of - At least, one network management station (NMS).
- Network management software running at the NMS is
also called a Network Manager - The Managed nodes (or devices) that are being
managed. - Those devices need to support a network
management protocol in order to communicate with
the NMS. Router is a typical example. - Network management software running at the
managed nodes is also called an Agent. - A protocol for communications, such as SNMP,
between Network Manager and Agents. - A set of information and configuration parameters
in Management Information Base (MIB) to be
monitored and controlled
16
Network Management Protocol
- Simple Network Management Protocol (SNMP)
supports networks using TCP/IP. - Has gained wide industry support due to the
popularity of Internet. - An application layer protocol that uses the User
Datagram Protocol (UDP). - SNMP uses port 161 for receiving query/request
and port 162 for receiving trap. - UDP is unreliable as compared to TCP. There is
no acknowledgment and message sequence numbering
with UDP. - However, UDP has a low overhead and it will not
flood a failing network with retransmissions.
17
SNMP Basic Operations
- Read operation is used by an SNMP manager (the
network management station) to monitor the agents
(the managed devices). The SNMP manager examines
the variables that are maintained by the agents. - Write operation is used by an SNMP manager to
control the agents. The SNMP manager sets the
values of variables stored in the agents. - Traversal operation is used by the NMS to
determine which variables a managed device
supports and to sequentially gather information
in variable tables (such as a routing table). - Trap operation is used by agents to report events
to the SNMP manager. When a certain event
occurs, the agent sends a traps (notification
messages) to the SNMP manager.
18
SNMP Read
- The read command is used by a network management
system (NMS) to monitor managed devices. - For instance, application programs in Linux (e.g.
net-SNMP) such as - snmpget specifies a single variable
system.sysDescr (1.3.6.1.2.1.1.1) - snmpget v 2c -c public router 1.3.6.1.2.1.1.1.0
- response returns value cisco 5505
- Snmpwalk reads a portion of the MIB sub-tree
from a device
19
SNMP Write
- The write command is used by an NMS to control
managed devices. - The NMS changes the values of variables stored
within managed devices. - snmpset
- snmpset -c private router 1.3.6.1.2.1.1.4.0
octetstring Meg A. Byte 555-1212 - system.sysContact.0 DISPLAY STRING- (ascii)
Meg A. Byte 555-1212
20
SNMP - Traversal Operations
- Traversal operations are used by the NMS to
determine which variables a managed device
supports and to sequentially gather information
in variable tables (such as a routing table). - Snmpget-next specifies OID, but value returned
is next lexicographic OID and its value - Get-next sysDescr, and you get sysObjectId
- Get-next sysObjectId and you get sysUpTime
21
SNMP Traps (1)
- Agent sends traps in the following situations
- coldStart (0)
- agent sends trap when initializing itself
- warmStart (1)
- agent sends trap when re-initalizing itself
- linkDown (2)
- specific link on the source device has failed
- linkUp (3)
- specific link on the source device has come up
22
SNMP Traps (2)
- authenticationFailure (4)
- agent determines that a request does not provide
proper authentication (e.g. wrong SNMP community
string) - egpNeighborLoss (5)
- agent reports the loss of an EGP neighbor
- enterpriseSpecific (6)
- implemented by a vendor to provide additional
functionality that complements the generic traps.
23
SNMP Community String
- SNMPv1 and v2 use "community strings" as a way of
establishing trust between network Managers and
Agents - A SNMP community string is a plain text password.
SNMP manager and agents using the same community
string are in the same community. A SNMP
community string is also called a SNMP community
name. - Types and usages of community strings
- Read-only for read (get) operation
- Read-write for read (get) and write (set)
operation - Trap community a community string for trap
operation
24
SNMP Polling Trap
Port 161
Port 162
25
SNMP Polling
- Polling is a request-response (client-server)
interaction between the SNMP manager and agents. - The SNMP manager (client) queries the agents
(managed devices), requests for various
information. The agent (server) responds with
information from its MIB. - The SNMP manager may use polling to obtain
information periodically. With more frequent
queries, more bandwidth are consumed.
26
SNMP Trap
- Trap
- An unsolicited notification sent by an SNMP agent
to a manager. - agents send messages to the manager the
initiative is with the agents, the manager has a
"listener" role and wait for incoming
information. - An agent sends a trap (notification message) when
a significant or an unusual event (a fault)
occurs, for example, - a change of state (an interface goes down or up)
- a critical threshold value is reached
- Event-triggered Traps may be better than Polling
- report problems as soon as they occur
- more efficient - if the states being monitored
dont often change - lesser bandwidth is consumed.
27
Versions of SNMP
- The Simple Network Management Protocol (SNMP) is
an application layer protocol that facilitates
the exchange of management information. - Three versions of SNMP
- SNMPv1
- Basic functions lacks security features
- SNMPv2 (version 2c)
- Some useful features, such as getBulk, are added.
- But still lacks security features
- SNMPv3
- Provides security features USM and VACM
28
MIB Object Identifiers
- Hierarchically structured
- Each object uniquely identified
SNMP AGENT
OID for system 1.3.6.1.2.1.1
proteon (1)
IBM (2)
cisco (9)
Internet Activities Board (IAB) Administered
Vendor Administered
29
MIB Objects
- MIB objects are identified by OIDs. An OID is a
series of numbers separated by dots. For
example, the OID for the MIB object sysUpTime is
1.3.6.1.2.1.1.3 - The top-level OIDs belong to different standards
organizations, while lower-level OIDs are
allocated by associated organizations. Vendors
can define private branches of OIDs for their own
products. - Object descriptor is a "name" for a MIB object.
The object descriptor for 1.3.6.1.2.1.1.3 is
iso.org.dod.internet.mgmt.mib-2.system.sysUpTime - The Net-SNMP tool snmptranslate helps convert
names and OIDs and provides other functions, for
examples - snmptranslate -Tp SNMPv2-MIBsystem
- snmptranslate -Td SNMPv2-MIBsystem
- snmptranslate -TB system
- snmptranslate -TB -On system
- snmptranslate 1.3.6.1.2.1.1.3
- Snmptranslate -Td 1.3.6.1.2.1.1.3
30
Examples of MIB Objects
Name of object type Abstract syntax of the
object type Object Identifier Access
type read-only, write-only,read-write, notify,
not-accessible Status type Mandatory, optional,
current deprecated, obsolete Description
textual definition of the object type
- sysUpTime OBJECT-TYPE
- SYNTAX TimeTicks
- ACCESS read-only
- STATUS mandatory
- DESCRIPTION
- "The time (in hundredths of a
second) since the - network management portion of
the system was last - re-initialized."
- system 3
- sysContact OBJECT-TYPE
- SYNTAX DisplayString (SIZE (0..255))
- ACCESS read-write
- STATUS mandatory
- DESCRIPTION
- "The textual identification of
the contact person - for this managed node, together
with information - on how to contact this person."
- system 4
31
Management Information Base (MIB)
- Management Information Base (MIB) is a collection
of managed objects (information) which are
organized hierarchically. - An Object Identifier (OID) uniquely identifies a
managed object. - A managed object (also called a MIB object, an
object, or a MIB) is one of the characteristics
of a managed device. - MIB objects are accessed (read/write) using a
network management protocol - SNMP. - Managed objects scalar and tabular.
- Scalar object defines a single object instance.
For example, atInput holds the integer value of
total number of input AppleTalk packets on a
router interface. - Tabular object defines multiple related object
instances that are grouped together in a MIB
table, e.g. ifTable.
32
MIB Scalar Objects (Instance 0)
- Scalar objects have only one instance of a
variable
OID for SNMP object sysContact 1.3.6.1.2.1.1.4
OID for SNMP variable Sal A. Mander 1.3.6.1.2.1.1.
4.0
33
MIB Multiple Instances
- Vector objects have appended instance suffixes gt0
to identify row in 2 dimensional tabular data
structures
mib-2 (1)
Conceptualized Table
row
1
value
2
3
column
34
Comparing SNMP, SMI and MIB
- SNMP defines the format of the packets exchanged
between SNMP managers and agents. These packets
contain the object names and their values. SNMP
is used to read/change these values. - SMI defines the general rules for naming objects,
defining object types, and showing how to encode
objects and values. - MIB creates a collection of named objects, their
types, and their relationship to each other in
the managed device. - Compare network management with writing a
program - Both tasks need rules in network management,
this is done by SMI. - Both tasks need variable declarations in network
management, this is done by MIB. - Both tasks need actions in network management
this is done by SNMP.
35
Structure of Management InformationSMI
- Functions of SMI
- To name objects
- To define the type of data
- To show how to encode data for transmission
- Name
- Each managed object has a unique name and an OID.
- An OID is a sequence of integers separated by
dots, for example, 1.3.6.1.2.1 - The name-dot notation (object descriptor) for the
OID 1.3.6.1.2.1 is iso.org.dod.internet.mgmt.mib-2
36
SMI Data Types
- SMI simple data types
- Integer signed integer in between
-2,147,483,648 to 2,147,483,647. - Octet strings ordered sequences of zero to
65,535 octets. - Object IDs
- SMI application-wide data types
- Network addresses represent an address from a
particular protocol family. SNMPv1 supports only
32-bit IP addresses. - Counters
- 32-bit (SNMPv1) or 64-bit counter (SNMPv2)
represents positive integers - counters can be incremented but not decremented
- when the maximum value is reached, the counter
returns (wrap back) to zero
37
SMI Data Types
- SMI application-wide data types
- Gauges are positive integers that can increase or
decrease but retain at the maximum value reached
(i.e. do not wrap back to zero) until being
reset. - A time tick represents a hundredth of a second
since some event. - An opaque represents an arbitrary encoding that
is used to pass arbitrary information strings
that do not conform to the strict data typing
used by the SMI. - An integer represents signed integer-valued
information. - An unsigned integer represents unsigned
integer-valued information and is useful when
values are always non-negative.
38
Counter
- A typical usage of Counter is measuring the
number of octets sent/received on an interface or
the number of errors and discards seen on an
interface within a period. The following is an
example of using Counter32 - Using counter32 to calculate data transferred
- Measure IF-MIBifOutOctets now, Nn
- Measure IF-MIBifOutOctets after 5 minutes, Nn1
- Traffic (Nn1-Nn)/time_difference bytes/sec
- Example
- N_1ifOutOctets at t_1 200000 bytes
N_2ifOutOctets at t_2 230000 bytes - t_2 t_1 5 minutes 300 seconds
- Number of bytes transferred 230000 200000
30000 bytes - bytes per second 30000/300 100 bytes per
second, or 800 bps
39
Counter and Gauge
- Both counter and gauge are used for measurement.
Due to their different operating characteristics,
they are used in different types of applications. - Since gauge can increase or decrease but not
exceed its maximum value (does not wrap back to
zero), it is suitable for measuring the current
value of some MIB objects, such as the current
number of packets in a queue/buffer, temperature,
CPU load, disk usage, etc..
40
Sequence and Sequence-of
- Two constructor types
- Sequence
- Consists of fixed amount of elements
- These elements may not be of the same data type
- Sequence-of
- Consists of one or more elements, all of the same
type. - Sequence and Sequence-of are used to construct
tables (tabular objects), as shown in the
following example.
41
SMI Encoding Method - BER
- SMI uses the Basic Encoding Rules (BER) to encode
data to be transmitted over the network. BER
specifies that each piece of data be encoded with
three fields Tag, Length and Value. - Tag a 1-byte long field that defines the type of
data. - Length If the fist bit of this field is 0, the
remaining 7 bits define the length of the data.
If the first bit is 1, the next 7 bits define the
number of bytes (excluding the first byte) needed
to define the length. - Value Value of the data.
42
Encoding tag
- To encode an integer 15.
- First, put hex 02 (binary 00000010) in the tag
field to indicate that it is an integer. - In the length field, put hex 04 because an
integer should be 4 bytes long. - In the value field, put 4 bytes of data 00 00 00
0F which is decimal 15.
43
Encoding length
- The length field is one or more bytes.
- If it is one byte, the most significant bit must
be 0. The other 7 bits define the length of the
data - If it is more than one byte, the MSB of the first
byte must be 1. The other 7 bits of the first
byte define the number of bytes needed to be
define the length. sequence of
44
Encoding value examples
- For example integer 14
- 02 04 00 00 00 0E Integer 4
byte value 00 00 00 14 - For example message HI
- 04 02 48 49 String 2 byte value
H I - format OID 1.3.6.1
- 06 04 01 03 06 01
- format IPAddress 131.21.14.8
- 40 04 83 15 0E 08
tag
length
value
45
Encoding exercise
- Show how the following array (sequence of) of
integers is encoded - 2345
- 1236
- 122
- 1236
- See note page for answer
46
Encoding exercise 2
- Show how following table (sequence) is encoded
- Integer String IP Address
- 2345 COMPUTER 185.32.1.5
- 2346 ROUTER
185.32.2.1 - See note page for answer
47
MIB-2 Objects
- Objects defined in MIB-2 (1.3.6.1.2.1) are
divided into ten groups system, interface,
address translation, ip, icmp, tcp, udp, egp,
transmission, and snmp.
48
Example of MIB definition, RFC12131.3.6.1.2.1.2
(..mib-2.interfaces)
49
Access MIB variables from udp group
50
Scalar Tabular objects udp
index
udpInDatagrams 1.3.6.1.2.1.7.1
1.3.6.1.2.1.7.5.1 udpEntry
200.1.1.1
444
1.3.6.1.2.1.7.5.1.2
1.3.6.1.2.1.7.5.1.1
1.3.6.1.2.1.7.5.1 udpEntry
udpNoPorts 1.3.6.1.2.1.7.2
1.3.6.1.2.1.7.5.1.2
1.3.6.1.2.1.7.5.1.1
udpInErrors 1.3.6.1.2.1.7.3
1.3.6.1.2.1.7.5.1 udpEntry
1.3.6.1.2.1.7.5.1.2
1.3.6.1.2.1.7.5.1.1
udpOutDatagrams 1.3.6.1.2.1.7.4
1.3.6.1.2.1.7.5 udpTable
51
Scalar Tabular objects udp
- To access scalar variables in the udp groups, use
the id of the group (1.3.6.1.2.1.7) followed by
the id of the variable. For example, - udpInDatagrams 1.3.6.1.2.1.7.1
- udpNoPorts 1.3.6.1.2.1.7.2
- These OIDs define the variables, but not the
instance (content of variable). To access the
instance, the instance suffix is needed. For
scalar variables, the instance suffix is 0. - udpInDatagrams.0 1.3.6.1.2.1.7.1.0
52
Tabular objects udpTable
- The OID of udpTable (the udp listener table) is
1.3.6.1.2.1.7.5 - The OID of an entry, the udpEntry is
1.3.6.1.2.1.7.5.1 - There can be multiple entries in the udpTable.
- Each entry in the table occupy one row.
- Each entry in the udpTable consists of two
fields - udpLocalAddress (an IP address)
- udpLocalPort (a port number)
- The OID of udpLocalAddress is 1.3.6.1.2.1.7.5.1.1
- The OID of udpLocalPort is 1.3.6.1.2.1.7.5.1.2
53
Tabular objects udpTable
- The udpTable can have several entries.
- To access the udpLocalAddress and udpLocalPort
fields of an udpEntry, an index should be added
to the OID. The index is based on both local
address and local port number, for examples - local address example 1 1.3.6.1.2.1.7.5.1.1.200.
1.1.1.444 - local address example 2 1.3.6.1.2.1.7.5.1.1.200.
2.2.2.555 - local port example 1 1.3.6.1.2.1.7.5.1.2.200.1.1
.1.444 - local port example 2 1.3.6.1.2.1.7.5.1.2.200.2.2
.2.555 - Other MIB tables are not indexed in the same way.
- udpTable is specified in RFC1213 and is
deprecated now, RFC4113 specifies a "new" table
called udpEndpointTable 1.3.6.1.2.1.7.7 - udpEndpointEntry consists udpEndpointLocalAddress,
udpEndpointLocalPort, udpEndpointRemoteAddressTyp
e, udpEndpointRemoteAddress, udpEndpointRemotePort
, udpEndpointInstance
54
SNMPv1 Protocol Operations
- Get operation is used by the SNMP manager to
retrieve the value of one or more object
instances from an agent. If the agent responding
(reply with a Response message) to the Get
operation cannot provide values for all the
object instances in a list, it does not provide
any values. - GetNext operation is used by the SNMP manager to
retrieve the value of the next object instance in
a table or list within an agent. - Set operation is used by the SNMP manager to set
the values of object instances within an agent. - Response operation is used by agents to reply the
SNMP manager with the requested information (MIB
objects and the associated values). - Trap operation is used by agents to notify the
SNMP manager of a significant event.
55
SNMPv2 Protocol Operations
- SNMPv2 supports the SNMPv1 Get, GetNext, and Set
operations. - SNMPv2 Trap operation serves the same function as
that used in SNMPv1, but it uses a different PDU
format and is designed to replace the SNMPv1
Trap. - In SNMPv2/v3, traps are also called
notifications. - SNMPv2 also defines the following protocol
operations - The GetBulk operation is used by the SNMP manager
to efficiently retrieve large blocks of data one
request asking for many objects. If the agent
responding to GetBulk operations cannot provide
values for all the variables in a list, it
provides partial results. - The Inform operation allows one manager to send
an alert to another manager and receive a
response (acknowledgment).
56
SNMP Protocol Data Unit PDU
- SNMPv1/2 messages contains PDU, version and
community fields. - SNMPv3 messages contains PDU and various fields
for security and other usages. - SNMPv1 Get/GetNext/Set/Response PDU contains
- PDU Type - specifies the type of PDU transmitted.
- Request ID - a sequence number to match a request
with response. - Error Status used by the Response PDU to show
the error type. In the Get/GetNext/Set PDU, this
is set to zero. - Error Index - used by the Response PDU to
associate an error with an object instance. In
the Get/GetNext/Set PDU, this is set to zero. - Variable Bindings - the data field each variable
binding associates an object instance with its
current value. The value is ignored in
Get/GetNext PDU.
57
SNMP Message Format
- SNMP message divided into four parts version,
header, security parameter and data - SNMP version
- version number (SNMPv1, SNMPv2 or SNMPv3)
- SNMP Header
- community string
- SNMP security parameter
- SNMP Data
- Context Engine ID
- Context Name
- PDU (see next page)
58
SNMP PDU
- Each SNMP PDU (except trap) has the following
format - PDU type
- request id - request sequence number
- error status - zero if no error otherwise one of
a small set - error index - if non zero indicates which of the
OIDs in the PDU caused the error2 - variable bind-list
- variable name - OIDs
- values - values are null for get and get next
59
Encoding SNMP message
- To encode a message, SNMP also uses the BER
standard - Message are defined using tags
- class
- format
- number gt for different type of message
Data Tag(Hex) GetRequest
A0 GetNextRequest A1 GetResponse
A2 SetRequest A3 Trap A7
60
Example Encoding GetRequest
- GetRequest (from NM station to router)
- 30 33
sequence of length 5133 (30 is tag for sequence
of) - 02 04 00 00 00 00 integer of length 4,
ver 0 (02 is tag for integer) - 04 06 70 75 62 6C 69 63 string of length 6,
public (04 is tag for string) - A0 23 GetRequest (A0), length 3523
(PDU) - 02 04 00 01 06 11 integer of length 4,
request 00010611 - 02 04 00 00 00 00 integer of length 4,
error status0 - 02 04 00 00 00 00 integer of length 4,
error index0 - 30 0F sequence of length 15
(VarBindList) - 30 0D sequence of length 13 (OID
Value) - 06 09 01 03 06 01 02 01 07 01 00 objectID of
length 9, -
(1.3.6.1.2.1.7.1.0) instance - 05 00 null entity of length 0
61
Example Encoding GetResponse
- GetResponse (from router to NM Station)
- 30 37 sequence of length 37(hex), 55(dec)
- 02 04 00 00 00 00 integer of length 4, ver 0
- 04 06 70 75 62 6C 69 63 string of length 6,
public - A2 27 GetResponse (A2), length 3927h
- 02 04 00 01 06 11 integer of length 4, request
00010611 - 02 04 00 00 00 00 integer of length 4, error
status0 - 02 04 00 00 00 00 integer of length 4, error
index0 - 30 13 sequence of length 1913(hex)
- 30 11 sequence of length 1711(hex)
- 06 09 01 03 06 01 02 01 07 01 00 objectID of
length 9,
(1.3.6.1.2.1.7.1.0) - 41 04 00 00 12 11 counter of length 04 with
value 12 11
62
Decoding Message Exercise
- Decode the following
- 02 04 01 02 14 32
- 30 0C 02 04 00 00 00 11 02 04 00 00 00 14
- 30 0B 04 03 41 43 42 02 04 00 00 14 14
- 30 0C 40 04 23 51 62 71 02 04 00 00 14 12
- See note page for answer
63
SNMP PDU
- SNMPv2/v3 PDU format for Get/GetNext/Inform/Report
/Response/ Set/Trap is similar to that of SNMPv1
Get/GetNext/Set/Response - SNMPv1 Trap PDU is different from SNMPv2/v3 Trap
PDU - SNMPv1 Trap PDU contains
- Enterprise - the type of managed object which
generates the trap. - Agent Address - the address of the managed object
which generates the trap. - Generic Trap Type - indicates the generic trap
type. - Specific Trap Code - indicates the specific trap
code. - Time Stamp - the time that has elapsed between
the last network (re)initialization and
generation of the trap. - Variable Bindings - the data field each variable
binding associates an object instance with its
current value.
64
SNMPv2/v3 GetBulk PDU
- SNMPv2/v3 GetBulk PDU consists the followings
- PDU Type - specifies the type of PDU.
- Request ID a sequence number to match a request
with response. - Non-repeaters - specifies the number (N) of
variables, starting from the first variable in
the variable bindings field in the request. One
variable binding is requested for each of the
these N variables. - Max-repetitions specifies the maximum number
(M) of variable bindings that are requested for
each of the remaining variables (R) in the
variable bindings field not covered by the
non-repeaters. - Variable Bindings - the data field each variable
binding associates an object instance with its
current value (value is ignored in
Get/GetNet/GetBulk). - Total variable bindings requested N MR
- N, M and R should not be negative
65
SNMP PDU
Get/GetNext/Set/Response/Trap/Inform PDU
GetBulk PDU
66
SNMP tool Net-SNMP
- Net-SNMP provides a tool snmpget that implements
the get request from a manager. For example,
requesting location of ictlab
snmpget v 2c c public ictlab
SNMPv2-MIBsysLocation.0 SNMPv2-MIBsysLocation.
0 STRING "Hong Kong, IVE(TY)/ICT"
- Net-SNMP commands
- snmpget
- snmpgetnext
- snmpwalk
- snmpbulkget
- snmpbulkwalk
67
Lexicographic ordering of OIDs the next value
- The ordering of the variables is
lexicographical as an object identifier is a
sequence of integers that reflects a hierarchical
or tree structure of the object in the MIB. - By using a traversal method, all nodes in a MIB
tree can be visited visit the root, then
traverse the sub-tree from left to right,
recursively - This ordering structure allows easy searching
ask for the value of next object without
specifying its name or OID.
68
Lexicographic ordering of a MIB tree
- Order of visiting the nodes
- 1
- 1.1
- 1.1.10
- 1.1.11
- 1.4
- 1.4.14
- 1.4.15
- 2
- 2.1
- 2.1.16
- 2.1.17
- 2.6
- 2.6.18
- 2.6.19
- 3
- 3.1
- 3.3
- 4
69
get-next-request
- SNMP manager sends a get-next-request. Agent
sends a response containing the value for the
next variable - Net-SNMP tools snmpgetnext, snmpwalk
snmpgetnext -v 2c c public ictlab
laLoad UCD-SNMP-MIBlaLoad.1 STRING 0.74
snmpwalk -v 2c c public ictlab laLoad
UCD-SNMP-MIBlaLoad.1 STRING
0.74 UCD-SNMP-MIBlaLoad.2 STRING
0.53 UCD-SNMP-MIBlaLoad.3 STRING 0.48
70
get-bulk-request
- SNMP manager sends a get-bulk-request for a
number of variables. Agent replies with a
response with as many answers as are requested,
or will fit in the PDU. - Much more efficient fewer requests and responses
required to fetch data - Net-SNMP tools snmpbulkget, snmpbulkwalk
snmpbulkget -v 2c -c public ictlab
laLoad UCD-SNMP-MIBlaLoad.1 STRING
0.62 UCD-SNMP-MIBlaLoad.2 STRING
0.66 UCD-SNMP-MIBlaLoad.3 STRING
0.59 UCD-SNMP-MIBlaConfig.1 STRING
2.00 UCD-SNMP-MIBlaConfig.2 STRING
4.00 UCD-SNMP-MIBlaConfig.3 STRING
4.00 UCD-SNMP-MIBlaLoadInt.1 INTEGER
61 UCD-SNMP-MIBlaLoadInt.2 INTEGER
66 UCD-SNMP-MIBlaLoadInt.3 INTEGER
58 UCD-SNMP-MIBlaLoadFloat.1 Opaque Float
0.620000
71
get-bulk-request non-repeaters, max-repetitions
1
snmpbulkget -v 2c C n2r3 c public ictlab
laLoad ifInOctets ifOutOctets UCD-SNMP-MIBlaLoad
.1 STRING 0.63 IF-MIBifInOctets.1
Counter32 35352440 IF-MIBifOutOctets.1
Counter32 35352440 IF-MIBifOutOctets.2
Counter32 297960502 IF-MIBifOutOctets.3
Counter32 0
- n2r3 Non-repeaters2, Max-repetitions3
- The first two variables laLoad and ifInOctets are
"non-repeaters" - One value of each of these two variables is
retrieved. - The max-repetitions value for the remaining
variable(s), ifOutOctets, is 3 - three values for the variable are asked for.
72
get-bulk-request nonrepeaters, max-repetitions
2
- snmpbulkget -v 2c C n1r3 c public ictlab
laLoad ifInOctets ifOutOctets - UCD-SNMP-MIBlaLoad.1 STRING 0.77
- IF-MIBifInOctets.1 Counter32 5356045
- IF-MIBifOutOctets.1 Counter32 5356045
- IF-MIBifInOctets.2 Counter32 1881446668
- IF-MIBifOutOctets.2 Counter32 3664336845
- IF-MIBifInOctets.3 Counter32 0
- IF-MIBifOutOctets.3 Counter32 0
- n1r3 Nonrepeaters1, Max-repetitions3
- One value for the first variable laLoad
- (non-repeaters 1)
- 3 values for the remaining variables ifInOctets
and ifOutOctets
73
get-bulk-request nonrepeaters, max-repetitions
3
- snmpbulkget -v 2c -C n3r3 -c public ictlab
laLoad ifInOctets ifOutOctets - UCD-SNMP-MIBlaLoad.1 STRING 0.71
- IF-MIBifInOctets.1 Counter32 35370916
- IF-MIBifOutOctets.1 Counter32 35370916
- n3r3 Nonrepeaters3, Max-repetitions3
- only one value is returned for each of the three
variables specified on the command line.
74
SNMPv1/v2 Security Problem
- Neither SNMPv1 nor SNMPv2 offers security
features only uses community string - Specifically, SNMPv1/v2 can neither authenticate
the source of a management message nor provide
encryption. - Without authentication, it is possible for
nonauthorized users to exercise SNMP network
management functions. - It is also possible for nonauthorized users to
eavesdrop on management information. - Because of these deficiencies, many SNMPv1/v2
implementations are limited to simple read-only
capability. Without implementing the set
operations, the SNMP is reduced to a monitoring
facility.
75
Network Security Risks
- Masquerading an unauthorized entity attempts to
perform network operations by assuming the
identity of an authorized entity. - Modification of information an unauthorized
entity attempt to modify a message generated by
an authorized entity so that the modified message
results in unauthorized operations. - Message sequence and timing modifications an
unauthorized entity reorders, delays or replays a
message generated by an authorized entity. - Disclosure an unauthorized entity extracts
values stored in the managed objects, or learns
events (traps) by monitoring the messages
exchanged between managers and agents.
76
SNMPv3 Security Services
- Authentication
- Check identity of user, verify username and
password - Data integrity
- Use hash function to check whether the data is
from the claimed identity, and whether the data
has been altered - Check the timeliness of data, check whether
messages are delayed or replayed (message stream
modification). - Data privacy encryption of data
- Access control (authorization)
- Assign different users with different levels of
access (no access, read, write, etc) to various
MIB objects.
77
SNMPv3 Entity, Engine, Context
- Each SNMPv3 entity includes an SNMP engine which
may implement functions for sending/receiving
messages, authentication, encryption and
controlling access to the MIB objects. - Each SNMP engine has an unique identifier called
snmpEngineID. - A contextName (or, context) is a collection of
management information accessible by an SNMP
entity. Access control is based on the specific
context for which access is requested, and the
identity of the user (the principal) requesting
the access.
78
SNMPv3 Principal
- A principal can be
- (i) an individual acting in a specific role,
- (ii) a group of individuals, with each acting in
a particular role, - (iii) an application or a set of applications or
- (iv) a combination of the above.
- A principal operates from a management station
and issues SNMP commands to the agents. The
identity of the principal and the target agent
together determine the security features that
will be invoked, including authentication,
privacy, and access control. - The use of principals allows security policies to
be tailored to the specific principal, agent and
the information exchanged. This enables human
security managers to assign authorization to
users more flexibly.
79
SNMPv3 Architecture
80
SNMPv3 Architecture - subsystems
- Dispatcher
- send and receive messages, determines version of
each received message - if received message can be handled, hands to
Message Processing Subsystem - Message Processing Subsystem
- prepares messages to be sent
- extracts data from received messages
- can have modules for each of SNMP v1, v2 and v3
(or other future type) - Security Subsystem
- provides authentication and encryption.
- uses MD5 or SHA algorithms to authenticate users
and DES or AES for encryption. - Access Control Subsystem
- implemented in SNMP agents
- controls access to MIB objects which objects,
and level of access
81
SNMPv3 Architecture - applications
- Each SNMPv3 entity has one or more applications
- The role of an SNMP entity is determined by the
applications that are implemented. Whether an
entity is a SNMP Manager or an Agent is
determined by the applications that it supports. - A traditional SNMP Manager may have the following
applications - Command Generator Applications
- Notification Receiver Applications
- Notification Originator Applications
- A traditional SNMP Agent may have the following
applications - Command Responder Applications
- Notification Originator Applications
- Proxy Forwarder Applications
82
User-Based Security Model (USM)
- Supports authentication, using hash function
- MD5 (Message Digest 5)
- SHA (Secure Hash Algorithm)
- Supports encryption using
- Data Encryption Standard (DES)
- Advanced Encryption Standard (AES)
- Supports individual user accounts
- USM uses the concept of authoritative engine.
- In any message transmission, either the
transmitter entity or receiver entity is
designated as the authoritative SNMP engine.
83
USM Rules for authoritative engine
- The receiver is authoritative
- If the SNMP messages expects a response.
- For example, message carrying Get, GetNext,
GetBulk, Set, or Inform PDU. - The sender is authoritative
- If the SNMP message does not expect a response.
- For example, message carrying Trap, Response or
Report PDU.
84
USM Timeliness Checking
- The authoritative SNMP engine provides a time
checking function. - The timeliness checking of a message is done by
the authoritative engine with respect to a clock
maintained by it. - An authoritative engine sends a message, such as
Trap and Response, with the current value of its
"clock". The receiver can synchronize on that
clock. - A nonauthoritative engine sends a message, such
as Get, with its current estimate of the time
value at the destination (the authoritative
engine). The receiver (the authoritative engine)
assess the timeliness of the message.
85
USM Authentication, Hash
- SNMPv3 authentication mechanism assures that a
received message - is transmitted by the principal whose identifier
appears as the source in the message header. - has not been altered during transmission
- is not artificially delayed or replayed.
- To achieve authentication, each pair of principal
and remote SNMP engines must share a secret key. - The sending entity use the secret key and hash
function to process the entire message in order
to generate a message authentication code. This
message authentication code is then added to the
message and then transmitted to the receiving
entity.
86
USM Authentication, Hash function
- The secret key must initially be set up outside
of SNMPv3 as a configuration function. The
network manager is responsible for distributing
initial secret keys to be loaded into the SNMP
managers and agents. - When the receiving entity gets the message, it
uses the same secret key and hash function to
calculate the message authentication code. If
this authentication code calculated by the
receiver matches the one in the incoming message,
the receiver assumes that the message is
authentic - the message is originated from the real source,
and - the message was not altered in transit.
- The message is further checked against its
timeliness - is it within a valid time window.
87
View-based Access Control Model (VACM)
- 5 elements of VACM
- Group, Security Level, Contexts, Views and Access
Policy - MIB View
- Restrict the access to only a subset of the
management information (i.e. a subset of the MIB
tree, or subtree) - A view subtree (a MIB view) is a pairing of an
OID value (the family name) together with a
family mask (or, view mask). - Security Levels
- (a) no authentication, no privacy,
- (b) authentication, no privacy
- (c) authentication and privacy
- Authentication MD5, SHA
- Encryption DES, AES
88
VACM
- Group - a set of one or more users
- All elements belonging to a group have equal
access rights - Different groups can be assigned different
security levels. - Based on the version of SNMP being used, groups
can be defined with different Security Models
(v1, v2c or USM). - Access Policy access depends on the following
factors - Type of access not accessible, read, write and
notify - Principal different access privileges for
different users - Security models different levels of access for
different models (SNMPv1, v2c or USM)
89
VACM example of MIB View
- The ifTable provides statistics on network
interfaces - one row in the table for each network interface
- the index, starting from 1, is the number at the
end of the OID. - An ISP wants to allow its customer X to view
their own network interface (such as index 5),
but not the network interfaces of others. The
required MIB view for customer X is - 1.3.6.1.2.1.2.2.1..5
- The symbol covers any number.
snmpbulkwalk -v 2c -On -c public localhost
ifTable .1.3.6.1.2.1.2.2.1.1.1 INTEGER
1 .1.3.6.1.2.1.2.2.1.1.2 INTEGER
2 .1.3.6.1.2.1.2.2.1.2.1 STRING
lo .1.3.6.1.2.1.2.2.1.2.2 STRING
eth0 .1.3.6.1.2.1.2.2.1.3.1 INTEGER
softwareLoopback(24) .1.3.6.1.2.1.2.2.1.3.2
INTEGER ethernetCsmacd(6) .1.3.6.1.2.1.2.2.1.4.1
INTEGER 16436 .1.3.6.1.2.1.2.2.1.4.2
INTEGER 1500 .1.3.6.1.2.1.2.2.1.5.1 Gauge32
10000000 .1.3.6.1.2.1.2.2.1.5.2 Gauge32
100000000 .1.3.6.1.2.1.2.2.1.6.1
STRING .1.3.6.1.2.1.2.2.1.6.2 STRING
013459912 .1.3.6.1.2.1.2.2.1.7.1 INTEGER
up(1) .1.3.6.1.2.1.2.2.1.7.2 INTEGER
up(1) .1.3.6.1.2.1.2.2.1.8.1 INTEGER
up(1) .1.3.6.1.2.1.2.2.1.8.2 INTEGER
up(1) .1.3.6.1.2.1.2.2.1.10.1 Counter32
1073820735 .1.3.6.1.2.1.2.2.1.10.2 Counter32
1620632733
90
VACM - View Mask
- One bit in the view mask determines access to one
component of OID. - A 0 in the view mask is like a wildcard for
don't care. - A 1 in the view mask matches the
corresponding OID component. - For the access control required in previous
slide, the following view mask (ff.a0 or ffa0)
can be used - As an example, the following pair of OID and view
mask provides the required MIB View - 1.3.6.1.2.1.2.2.1.1.5 ff.a0
91
Remote Monitoring RMON
- A weakness of SNMP is its request-response
operation can result in the significant
degradation of lower operating rate WAN
bandwidth when monitoring geographically
separated networks. - By defining a Remote Monitoring MIB (RMON) is a
major step forward in internetwork management. - RMON extensions to SNMP give the ability of the
SNMP manager to look at the network as a whole as
opposed to looking at individual devices. - When working with RMON, there is no change in the
underlying SNMP protocol. A central management
console is the point of data collection. An RMON
probe is located on each segment of the network
monitored. - A probe has the same function as a SNMP agent.
These probes can be dedicated hosts, resident on
a server, or included in a standard networking
device such as a router or switch. - These RMON probes/agents operate in promiscuous
mode to gather the specified data from each
segment and relay it to the management console. - The RMON extension to the SNMP protocol defines
standard network monitoring functions and
interfaces for communicating between SNMP-based
management consoles and remote monitors.
92
How RMON Works
- RMON is an example of a 3-tier organization.
- The RMOM probe layer plays the dual role
- Agent to the top-level manager
- Manager to the managed objects
- This enables MIB information to be stored on the
device itself or on distributed RMON probes that
store MIB information closer to the devices that
generate it. - No transmission from MIB to the manager until it
requesting the data. - RMON reduces network traffic
93
RMON as an extension of SNMP
- RMON is network monitoring and analysis standard
similar to SNMP. - limitations of SNMP in traffic monitoring
- NM need to continuously retrieve MIB information
from agents or - agents need to continuously update NM by trap gt
too much overhead - RMON provide a better model to collect network
traffics - agent (in SNMP) gt probe (in RMON)
- a more intelligent, software process running on
network devices to collect information and store
it in a local MIB - to improve efficiency of carrying of network
traffic trends - in SNMP gt NM need to poll devices continuous and
calculate the trends (requires heavy traffic and
CPU loading on NM station) - in RMON gt probe carry out the traffic trend
locally and only update the NM with the traffic
trends
94
RMON-Probe
- Probes similar to agents in SNMP
- Software processes running on network devices to
collect information about network traffic and
store it in a local MIB
95
RMON MIB, RMON Groups
- Each RMON group provides specific sets of data
each group is optional, vendors do not need to
support all the groups. - However, some RMON groups require support of
other RMON groups, for example, the alarm group
needs the event group. - RMON MIB is incorporated into the MIB-II. The
OIDs of RMON MIB start with the prefix
1.3.6.1.2.1.16 (i.e. mib-2.16) - RMON1 (original RMON) groups of MIB objects
- statistics history alarm host hostTopN
matrix filter packet capture event token ring - RMON2 adds the following groups
- protocol directory protocol distribution
address mapping network layer host NL matrix
application layer host AL matrix user history
probe configuration rmonConformance
96
RMON1 and RMON2
- The original RMON MIB is limited to MAC level
operations. RMON1 probes can monitor all traffic
on the network by capturing data frames and read
the MAC addresses in those frames. Hence, RMON1
cannot determine the real sources and
destinations of traffic coming/leaving via the
router. - RMON2 probes can read network-layer protocol (IP
addresses). - RMON2 probes can also read details in the
higher-layer headers, such as TCP port numbers,
i.e. they can know the applications. Hence,
RMON2 can produce network traffic statistics on
the basis of application.
97
RMON Groups