AAA Services - PowerPoint PPT Presentation
1 / 15
Title:
AAA Services
Description:
... AAA RADIUS vs TACACS+ RADIUS Remote Authentication Dial In User Service An ... shtml T. A. Yang Network Security * RADIUS Example Clients: router ... – PowerPoint PPT presentation
Number of Views:101
Avg rating:3.0/5.0
Title: AAA Services
1
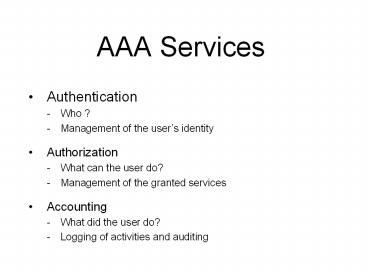
AAA Services
- Authentication
- Who ?
- Management of the users identity
- Authorization
- What can the user do?
- Management of the granted services
- Accounting
- What did the user do?
- Logging of activities and auditing
2
Uses of AAA
- Two modes
- The character mode access
- AAA services are used to control administrative
access such as Telent or Console access to
network devices - The packet mode access
- AAA services are used to manage remote user
network access such as dialup clients or VPN
clients
3
c.f., Alternative methods to AAA
- Examples
- Password-based authentication
- Challenge-response authentication
- Incomplete access management
- Limited to authentication only
4
Local vs Centralized Databases in AAA
Features Local dB Centralized dB
Location of user data local on the device In a central authentication server (remote to the device)
Copies of user data Multiple copies (one per device) Single copy
Scalability Poor (Given a change, each copy needs to be updated.) Good
Single-point failure ? Depends (possibly no) Yes
Recommended ? Only for very small networks Yes (especially for larger networks)
5
Authentication Protocols in AAA
- RADIUS vs TACACS
- RADIUS
- Remote Authentication Dial In User Service
- An IETF standard (RFC 2865)
- Open source s/w
- Interoperability among RADIUS-based products
- Client/server authentication btwn a NAS (e.g., a
router) and a RADIUS server - A shared secret btwn the client and the server
- on UDP (port 1812 for authentication and
authorization port 1813 for accounting)
6
RADIUS
- RFC 2865 (2000) http//www.ietf.org/rfc/rfc2865.t
xt
7
The Authenticator field
- Request Authenticator
- The authenticator in the Access-Request packets
- Rqts The value SHOULD be unpredictable and
unique over the lifetime of a shared secret - Repetition of a request value in conjunction with
the same secret would permit an attacker to reply
with a previously intercepted response. - Response Authenticator
- The authenticator in the Access-Accept, Access-
Reject, and Access-Challenge packets - ResponseAuth MD5(CodeIDLengthRequestAuthAttr
ibutesSecret)
8
RADIUS
- http//www.cisco.com/en/US/tech/tk59/technologies_
tech_note09186a0080094e99.shtml
- Example Clients router, switch, PIX/ASA, VPN3000
- The Access-Request contains username, encrypted
password, NAS IP address, NAS port number, and
session information.
9
RADIUS authentication
- Note Both authentication and authorization
information are combined in a single
Access-Request packet. - Upon receiving an Access-Request, the RADIUS
server - Validates the shared secret
- Validates the username and password
- If not validated, sends an Access-Reject
response - Authorizes the user
- If authorization fails, sends an Access-Reject
response - Otherwise, sends an Access-Accept response
10
Security mechanisms in RADIUS
- Shared secret btwn the client and the server
- In the Access-Request packet, the password is
encrypted. - MD5 (shared secret Request
Authenticator) - XOR the-first-16-octets-of-the-password
- 16-octet encrypted password
- Q How would the RADIUS server authenticate the
encrypted password?
11
TACACS
- TACACS Terminal Access Controller Access Control
System - A Cisco proprietary client/server authentication
protocol - A shared secret btwn the client the server
- Can encrypt the entire body of the packet (as
indicated by the flags field) - On TCP
12
TACACS
- http//tools.ietf.org/html/draft-grant-tacacs-02
13
TACACS
- Example interactions http//www.cisco.com/en/US/t
ech/tk59/technologies_tech_note09186a0080094e99.sh
tml
14
TACACS vs RADIUS
- Shared
- Client/server based
- Authentication btwn a NAS and an authentication
server - Shared secret
- Differences ?
15
TACACS vs RADIUSsource http//etutorials.org/N
etworking/networkmanagement/PartIIImplementatio
nsontheCiscoDevices/Chapter9.AAAAccounting/
High-LevelComparisonofRADIUSTACACSandDiamete
r/
Criterion TACACS RADIUS
Transport TCP (reliable more overhead) UDP (unreliable higher performance)
Authentication and Authorization Can be separated (more flexible) Combined
Multiprotocol Support Supported (IP, Apple, NetBIOS, Novell, X.25) IP only
Access to Router CLI Commands Supports two methods to control the authorization of router commands on a per-user or per-group basis Not supported
Encryption Packet payload Passwords only