Biometric Access Control - PowerPoint PPT Presentation
1 / 12
Title:
Biometric Access Control
Description:
Virtual Private Infrastructure (VPI) connects remote devices over the Internet ... using the devices and it is guarantied the washing machine ... – PowerPoint PPT presentation
Number of Views:81
Avg rating:3.0/5.0
Title: Biometric Access Control
1
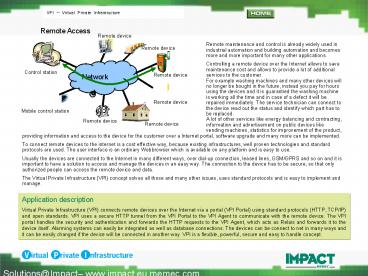
Remote maintenance and control is already
widely used in industrial automation and
building automation and becomes more and
more important for many other applications. C
ontrolling a remote device over the Internet
allows to save maintenance cost and allows
to provide a lot of additional services to
the customer. For example washing machines
and many other devices will no longer be
bought in the future, instead you pay for
hours using the devices and it is guarantied
the washing machine is working all the time
and in case of a defect it will be repaired
immediately. The service technician can connect
to the device read out the status and
identify which part has to be
replaced. A lot of other services like
energy balancing and contracting, information
and advertisement on public devices
like vending machines, statistics for
improvement of the product,providing information
and access to the device for the customer over a
Internet portal, software upgrade and many more
can be implemented. To connect remote devices to
the internet is a cost effective way, because
existing infrastructures, well proven
technologies and standard protocols are used. The
user interface is an ordinary Webbrowser which is
available on any platform and is easy to
use. Usually the devices are connected to the
Internet in many different ways, over dial-up
connection, leased lines, GSM/GPRS and so on and
it is important to have a solution to access and
manage the devices in an easy way. The connection
to the device has to be secure, so that only
authorized people can access the remote device
and data. The Virtual Private Infrastructure
(VPI) concept solves all those and many other
issues, uses standard protocols and is easy to
implement and manage.
Application description Virtual Private
Infrastructure (VPI) connects remote devices over
the Internet via a portal (VPI Portal) using
standard protocols (HTTP, TCP/IP) and open
standards. VPI uses a secure HTTP tunnel from the
VPI Portal to the VPI Agent to communicate with
the remote device. The VPI portal handles the
security and authentication and forwards the HTTP
requests to the VPI Agent, which acts as Relais
and forwards it to the device itself. Alarming
systems can easily be integrated as well as
database connections. The devices can be connect
to net in many ways and it can be easily changed
if the device will be connected in another way.
VPI is a flexible, powerful, secure and easy to
handle concept.
2
Alarming / SMS / e-mail / Report DB
VPI Overview
Control (Office)
Coach
VPI Initiative
Intranet (Management) Service Company
Service Control (Home)
Firewall
Leased Line
VPI Portal
ISP
Dial-up / GSM / GPRS
Internet
ISP
Device
SSL
Leased Line
Device
Dial-up
VPI Agent
Firewall
LAN Customer B
Device
VPI Agent
LAN Customer A
Device
Device
Device
Device
Device
Acronyms
Device
3
Virtual Private Infrastructure - iniNet
- For the monitoring and controlling of devices,
the remote access via a web browser to an
embedded webserver of a distant system is a
widely used technology. Generally, by means of
PPP (Point to Point Protocol), a temporary
point-to-point connection via a telephone line is
made. For cost and security reasons, however, the
systems to be monitored have neither a permanent
or a transparent Internet access. - iniNet AG has developed a new concept with the
SpiderControl VPI which integrates existing
company networks and infrastructures and does not
require additional connections. With the
SpiderControl VPI, distant systems can be called
up at all times in the same way as with a
permanent connection. Firewalls, routers and
switches are no handicap, and do not have to be
reconfigured. The VPI offers a high degree of
security and is also used in the banking sector. - The VPI-agent allows you to reach your device via
the Internet even if this is behind a firewall
and does not have a public TCP/IP number. - The operator of the intranet has control over the
VPI-agent and can define at any time which target
systems should be imaged on the Internet. Through
the Internet Service Provider (ISP) the VPI-agent
keeps a tunnel to a central webserver on the
Internet (or VPI-portal). A user now selects the
address of this server and must identify himself
with his user name and password. - Subsequently, this user receives a list with the
links (direct on the target system) to which he
has right of access. If the user selects such a
target, the connection is now taken up fully
transparent and maintained via the marked route. - The VPI-agent is a software module which can be
operated on any system within the intranet. A PC,
a server or a suitably embedded device can be
used for this. - Features
- Data traffic runs over the Internet via Secure
Socket Layer (SSL) - User identification with user name and password
- Each access can be logged
- Access is realised on application level instead
of protocol level - The connection can be activated from the device
only when required - The whole tunnel can be closed at any time
without having any effect on normal operation of
the network whatsoever
4
VPI Portal
- The VPI Portal is provided by a Internet Service
Provider (ISP). A user selects the address of
this server and must identify himself with his
user name and password. Subsequently, this user
receives a list with the links of target systems
to which he has right of access. If the user
selects such a target, the connection is now
taken up fully transparent via the marked route. - Features
- ISP guarantees internet access
- Maintain user accounts, access rights
- Solves security
- Provides access to the remote devices
- Portal Requirements
- Transparent forwarding of HTTP-protocol
- SSL Encryption
- Multiple communication channels
- Leased line, GSM, GPRS, dial-out, analogue, ISDN,
wireless - Manual and automated use
5
VPI Agent
- The VPI Agent is used to make devices within an
intranet accessible from the VPI-Portal. The
operator of the intranet has control over the
VPI-Agent and can define at any time which target
systems should be imaged on the Internet. Through
the Internet Service Provider (ISP) the VPI-Agent
keeps a secure tunnel to a central to VPI-Portal
on the Internet. The VPI-agent is a software
module which can be operated on any system within
the intranet. A PC, a server or a suitably
embedded device can be used for this. - Features
- Similar technology as VPN, but on a device level
not on a network level - Secure, encrypted tunnel to the VPI Portal
- HTTP-Relais
- No TCP/IP routing to the Internet
- Customer (end-user) has control over the
connection - No reconfiguration of IT infrastructure needed
- Physical connection interchangeable, leas-line,
ADSL, ISDN, Modem, GPRS, - Easy configuration
6
Remote Device
- Any device with an embedded Web server can be
used with VPI. - Web servers can be implemented in many different
ways, as fully integrated, as add-on solution or
gateway solution, depending on the requirements.
p_at_ac is a comprehensive system solution for
embedded internet connectivity, it supports
multiple platforms and uses SpiderControl
software and is fully VPI compatible. (See next
pages) - For examples of applications for remote
maintenance and control see the various System
Solutions _at_ Impact - Requirements of the embedded Web server for VPI
- All services implemented on HTTP
- Remote Procedure Calls, for reading and writing
variables - File transfer over HTTP (POST, GET)
- No absolute URL addresses to the server itself
- System Solutions _at_ Impact
- Vending Machine
- Utility meter
- Remote Heating Control
- POS Terminal
- Biometric Access Control
- Patient Monitoring
- Data logger
Remote Device
Application
HTML pages Java Applets
Application
Application Software
Network
Web Server
Data Server
Software
Webserver
Application
TCP/IP
TCP/IP
PPP
RTOS
Modem
Ethernet
GSM/GPRS
7
Remote Device
Integrated Solution
The Integrated Solution uses one Microcontroller
for both, the connectivity and the application. A
Real Time Operating System handles the
application and communication task. The Network
Interface can be integrated in the controller or
externally, for example a GSM interface would be
externally and Ethernet can could be integrated.
Remote Device
Network
Network Interface
Micro Controller
Power Supply
Interfaces
Add-on Solution
The add on solution uses a connectivity card or
box plugged in or hooked up to the Remote Device,
which has its on micro controller. The micro
controller on the connectivity card handles the
network protocols and the web server. The two
controllers are connected over a serial or
parallel link and use a simple protocol to
communicate.
Remote Device
Connectivity Card/Box
Network
Network Interface
Host Micro Controller
Micro controller
Power Supply
Interfaces
Gateway Solution
In a Gateway Solution the resource intensive
tasks like Network Interface, TCP/IP Stack and
common data is handled by the gateway. Multiple
Devices can be connected to the gateway over
wired or wireless connection. On the gateway are
the device dependent data and the application
code. In the gateway approach the SpiderControl
Distributed Webserver is used, which allows to
use Java-Applet and HTML pages to control also
for small Remote Devices with limited resources.
Remote Device
Remote Device
Comm. Interface
Micro controller
Power Supply
Gateway
Remote Device
Comm. Interface
Micro controller
Network
Power Supply
Network Interface
Comm. Interface
Micro Controller
Comm. Interface
Micro Controller
Power Supply
Interfaces
Interfaces
Interfaces
Serial line, Bluetooth, Modem, GSM, GPRS,
8
Remote Device
Hardware
The NEC micro controllers are well suited for
embedded Internet connectivity. NEC has a wide
range of micro controllers from 8 - 64Bit and
Impact can offer multiple solutions and reference
design for embedded Internet connectivity.
Contact Impact for details on the NEC micro
controller and micro controllers from Analog
Devices and Xilinx Solutions.
Software
pacNET
The pacNET software packages are optimised for
embedded applications with NEC micro controllers.
They contain SpiderControl software and are fully
VPI compatible. The pacNETweb includes the embOS
Realtime Operating System (Segger), TCP/IP stack,
Web server (SpiderControl, iniNet) and Drivers.
Multiple protocol stacks and software packages
are available, optimised for different
requirements.Contact Impact for details.
pacNETweb
WEB-Server
TCP/IP
embOS
Drivers
9
Control- / Service-Station
- The control station for remote controlling the
devices can be any PC, Workstation, Notebook, PDA
with a Webbrowser. With the browser you access
the remote device via the VPI Portal. Java
Applets are loaded from the device, providing a
user friendly interface to control the device. - Any service technician can access the VPI Portal
from anywhere. For example from his home, office,
car . - Of course it is also possible to use an automated
process to control the remote devices, exchange
data with the devices, store it in a database,
generate alarm messages, initiate firmware
upgrades, etc. - Features
- Only webbrowser needed for remote contrlol
- Access remote device via VPI Portal
- Interactive or automated control of remote
devices - Easy to use
10
VPI Initiative
VPI-initiative An industry initiative for the
secure accessibility of Embedded systems over the
Internet The Virtual Private Infrastructure (VPI)
- Initivative is an industry initiative for
instrument manufacturer, service provider,
software manufacturer, machine manufacturer and
engineering companies. The purpose of the
association is the promotion of the VPI-standard,
to achieve a homogeneous accessibility of systems
to Internet for remote control, maintenance and
service solutions in the industrial
environment. Goal and benefits of the
VPI-initiative The aim of the initiative is to
make several companies from different sectors
pursuit the same vision and communicate it to the
market. Customers should be offered an open,
seminal concept that is supported by many
independent companies which are anchored within
their respective markets. The companies benefit
from their involvement by offering VPI
compatible solutions for their existing products
they can open up new markets and thus enlarge
their market potential.
Members of VPI Initiative iniNet AG Impact, Memec
AG Aartec AG Ascom Systec AG Dätwyler Electronics
AG emazy corporation Mitsubishi International
GmbH Rolitec AG SAIA-Burgess Controls
AG Selectron Systems AG SSV Software Systems
GmbH Syslogic Datentechnik AG Tixi.Com
GmbH TRUMPF Laser Marking Systems AG TRUMPF Laser
GmbH Co. KG unimontis AG The list of members is
rapidly growing
http//www.vpi-initiative.com
11
Acronyms 1/2
- ISP
- Firewall
- Internet
- WAN
- Intranet
- LAN
- VPI
- URL
- IP
- IP address
- TCP
- UDP
Internet Service Provider, a company or
organization that provides connections to the
Internet to companies or individuals via dial-up,
ISDN, leased lines, or other connections. System
designed to defend against unauthorized access to
or from a private network. Firewalls can be
implemented in both hardware and software, or a
combination of both. A worldwide interconnection
among or between private, industrial or
governmental computer networks. -gt WANNote- The
Internet originally served to interconnect
laboratories engaged in government research, and
has now been expanded to serve millions of users
and a multitude of purposes, such as
interpersonal messaging, computer conferences,
file transfer, and consulting of files containing
documents. Wide Area Network connects LANs
together. The networks that make up a WAN can be
located throughout a country or even around the
world. The Internet is currently the largest
WAN. Any private network that uses the internet
protocols. The intranet may be connected to The
Internet via firewalls, or it may be totally
separate. Local Area Network, connects computers
and devices close to each other such as on one
floor of a building, one building, or a
campus. Virtual Private Infrastructure Uniform
Resource Locator, a character string describing
the location and access method of a resource on
the Internet. Example, the URL http//www.impact.c
h.memec.com/pac describes the type of access
method being used (http) and the server location
which hosts the Web site. Internet Protocol,
standard protocol for transmission of data from
source to destinations in packet-switched
communications networks and interconnected
systems of such networks. Sources and
destinations are hosts identified by an IP
address. A devices or resources numerical
address as expressed in the format specified in
the Internet Protocol. Transmission Control
Protocol, standard, connection- oriented,
full-duplex, host-to-host protocol used over
packet-switched computer communications networks.
User Datagram Protocol, a standard, low-
overhead, connectionless, host-to-host protocol
that is used over packet-switched computer
communications networks.
12
Acronyms 2/2
- HTTP
- HTTPS
- SSL
- SMTP
- DHCP
- FTP
- TELNET
- PPP
- DNS
- SNMP
Hypertext Transfer Protocol is a widely used
protocol to transfer information over the
Internet. Typically, it is used to transfer
information from Web Servers to Web
Browsers. Secure HyperText Transfer Protocol is a
protocol to transfer information securely over
the Internet. HTTPS encrypts and decrypts
information exchanged between a Web server and a
Web browser using Secure Socket Layer
(SSL). Secure Socket Layer, a method to encrypt
communications between two parties over the
Internet, by means of authentication, privacy and
integrity services that are inserted between the
Sockets interface and the TCP/IP stack. SSL uses
symmetric or asymmetric (public key) cryptography
for peer authentication. Simple Mail Transfer
Protocol, a protocol used to transfer
e-mail. Dynamic Host Configuration Protocol
allows communication between network devices and
a server that administers IP addresses. A DHCP
server leases IP addresses and other TCP/IP
information to DHCP client that requests them.
Typically, a DHCP client leases an IP address for
a period of time from a DHCP server which allows
a larger number of clients to use a set pool of
IP addresses. File Transfer Protocol, is used
to transfer documents between different types of
computers on a TCP/IP network. Terminal
Emulation Protocol, is used for remote terminal
connection service and that allows a user at one
site to interact with systems at other sites as
if that user terminal were directly connected to
computers at those sites. Point to Point
Protocol, is the communication protocol that
works with a modem and allows a computer to
communicate with the ISP's server. Domain Name
Server, a server within the Internet network that
performs translation between fully qualified
domain names and IP addresses according to the
domain name system. Simple Network Management
Protocol, a standard protocol that is used to
manage and control IP gateways and the networks
to which they are attached.